Trace Labs Challenge #14

Hey everyone — Yeti here, boots laced, goggles frosted, wrapping up the final Trace Labs challenge of 2025.
This one is a beautiful mix of technical OSINT, visual analysis, and contextual reasoning — exactly the kind of investigation that mirrors real-world work.
Let’s dig in. 🧊
Objective
Suspicious network traffic was observed during monitoring.
A screenshot from the same session may help identify the location.
One HTTP header appears out of place.
Our goal: identify the real-world location tied to this traffic.
Tools Used
- Google Images
- Google Maps
- Base64 Decoder
Screenshot:

Http Header:
HTTP/1.1 200 OK
Server: Apache/2.4.57 (Ubuntu)
Content-Type: text/html; charset=UTF-8
X-Powered-By: PHP/8.2.0
X-Clue: U2FuZHMgTGlmZXN0eWxlIENvdW50ZXIgKEhvdGVsIExvYmJ5KQ==
Cache-Control: no-cache
Connection: closeStep 1: Identify the Anomaly
Most of these headers look perfectly normal… except one:
X-Clue
- Non-standard
- Long
- Encoded
- Intentionally placed
Whenever you see custom headers with encoded content, assume it’s deliberate.
This is our entry point.
Step 2: Decode the X-Clue (Base64)
We take the value:
U2FuZHMgTGlmZXN0eWxlIENvdW50ZXIgKEhvdGVsIExvYmJ5KQ==
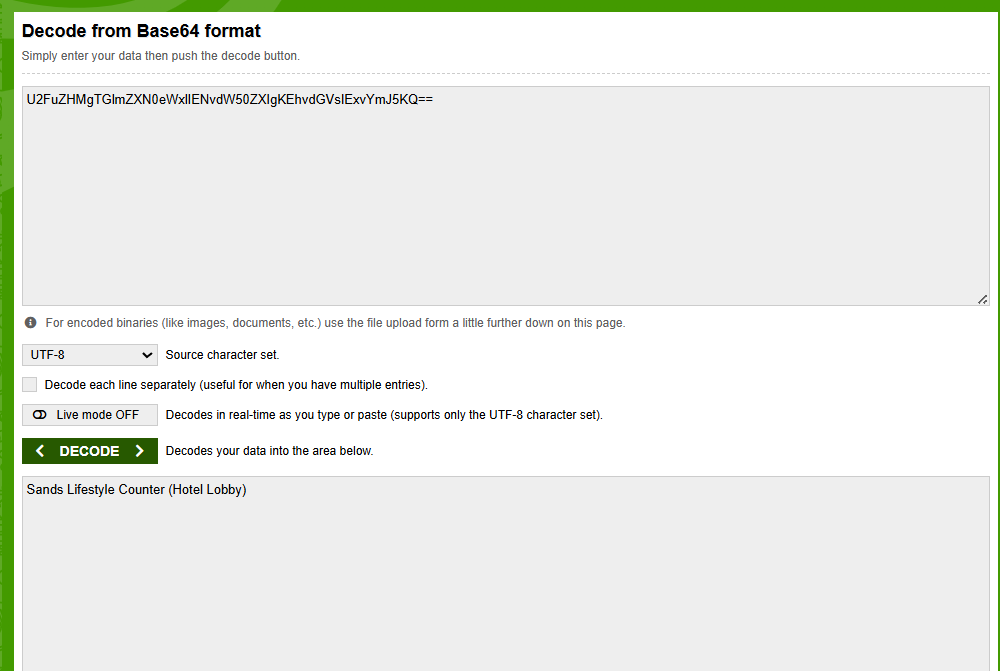
Drop it into a Base64 decoder.
Decoded Result:
“Sands Lifestyle Counter (Hotel Lobby)”
That’s not noise — that’s a semantic clue.
Two things immediately stand out:
- “Sands”
- “Hotel Lobby”
We now have a conceptual location
Step 3: Reverse Image Search the Screenshot
Now we pivot to the second artifact: the screenshot.
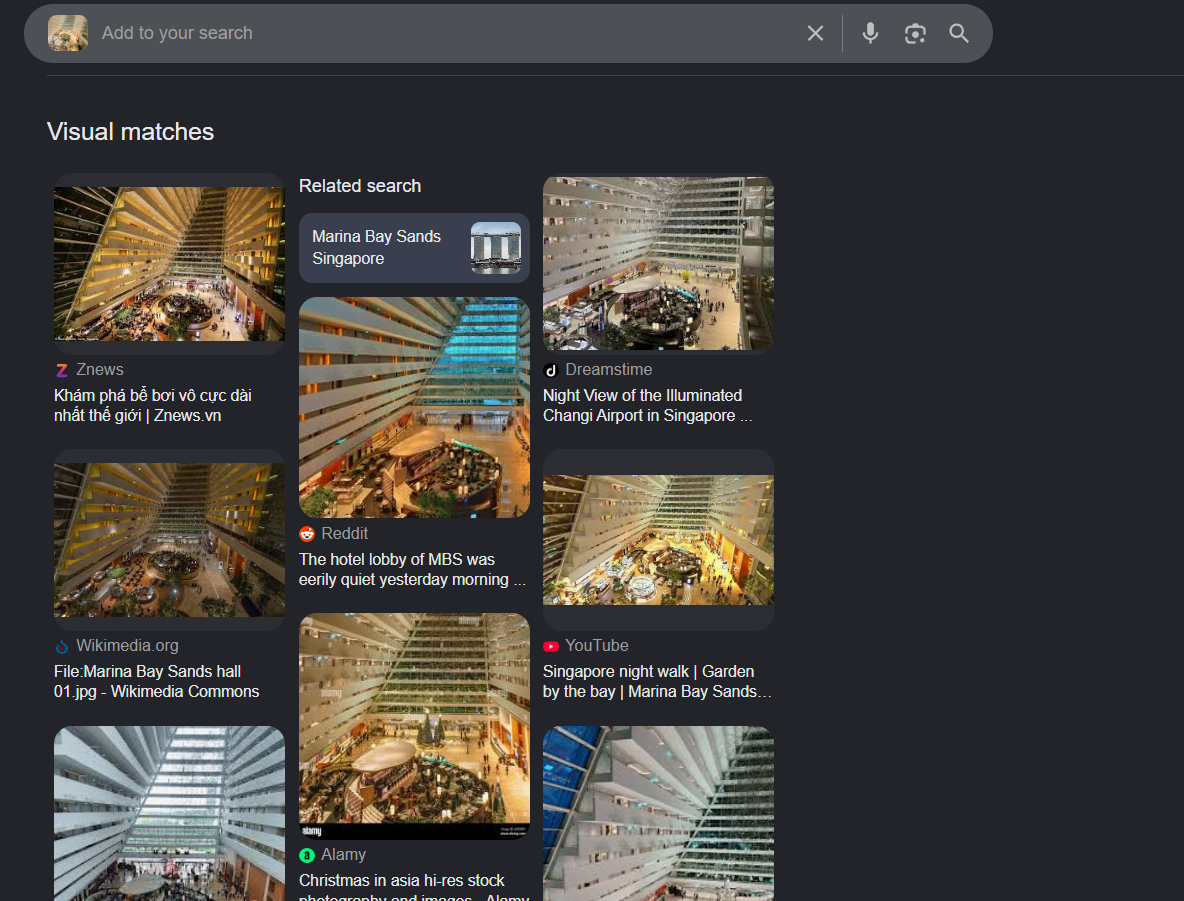
Uploading it to Google Images returns several strong visual matches:
- Marina Bay Sands
- Singapore skyline
- Interior hotel lobby shots
- References to the Sands complex
This aligns perfectly with our decoded header.
We now have two independent signals pointing to the same place:
- Encoded technical metadata
- Visual confirmation
That’s solid OSINT.
Step 4: Pivot to Maps for Ground Truth
Time to verify visually.
We open Google Maps and search for:
Sands Lifestyle Counter Singapore
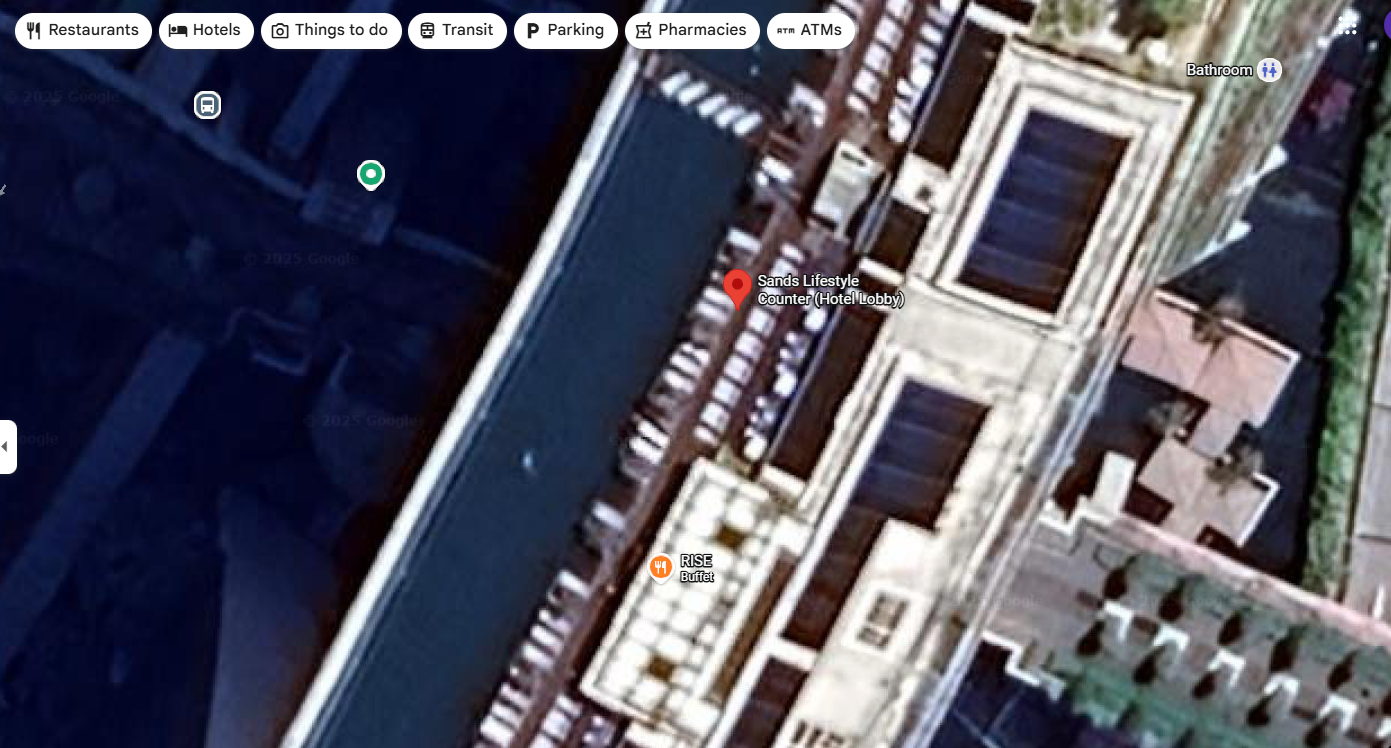
Using Street View:
- We scan lobby-level interiors
- Compare layout, lighting, counters, signage
- Match architectural features from the screenshot
💡 Pro tip:
Hovering Pegman over indoor-accessible locations often reveals preview images before committing — incredibly useful for hotel interiors.
The match is undeniable.

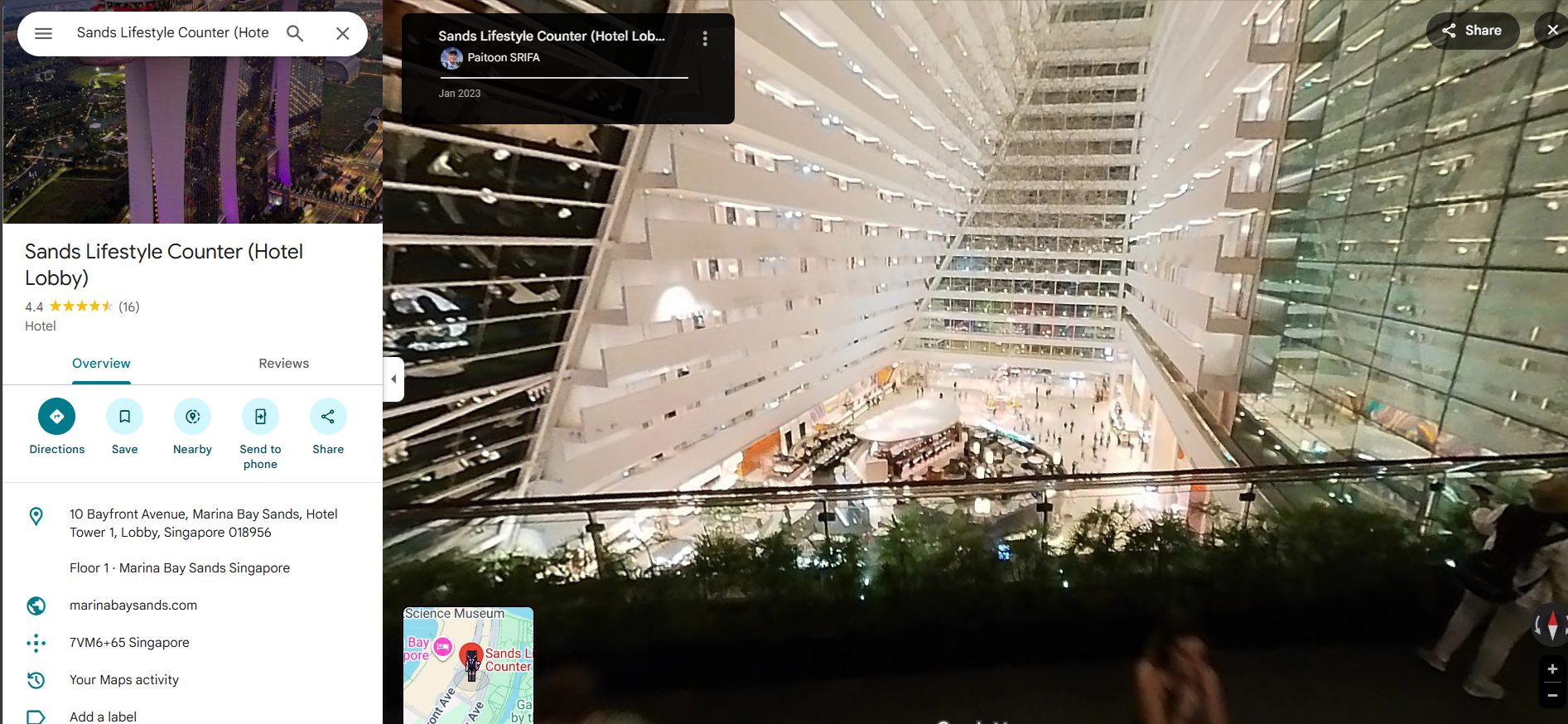
so now we have visual confirmation of our screenshot and we have successfully located where the suspicious traffic was coming from
Final Answer: Marina Bay Sands Hotel Lobby, Singapore
Why This Matters
This challenge is a perfect example of multi-layered OSINT:
- A single HTTP header told us where to look
- An image told us what to confirm
- Context tied everything together
In real investigations, this technique applies to:
- Threat infrastructure attribution
- Incident response
- Insider threat analysis
- Network forensics
- CTI enrichment
Technical artifacts rarely exist in isolation — context is everything.
Final Thoughts from the Yeti
This challenge wasn’t about hacking.
It was about thinking.
- Read the headers
- Decode the clues
- Trust, but verify
- Correlate multiple data sources
That’s OSINT done right.
Thanks for running these Trace Labs challenges with me all year.
2025 was a big one — and 2026 is going to be even colder. ❄️