🧊 SQL Injection Attack: Breaking into Admin on OWASP Juice Shop

Hey everyone, it’s Yeti back again, and lately I’ve been sharpening my claws on some bug bounty practice — diving into one of the best playgrounds for web app security: OWASP Juice Shop! 🍹
This app is modern, full of real-world scenarios, and absolutely loaded with vulnerabilities just waiting to be pounced on. In today’s post, I’m walking you through Authentication Bypass using SQL Injection — a classic, yet devastating attack when executed correctly.
What’s Authentication Bypass?
For those new to the game — authentication bypass is when you gain access to a user account (or admin!) without knowing the password or even having an account. You're skipping the front gate like a ninja with a master key.
Initial Recon: Shopping for Vulnerabilities
Once I landed on Juice Shop, I saw a list of purchasable items. Naturally, I clicked around and spotted an Apple Juice product with a user review.
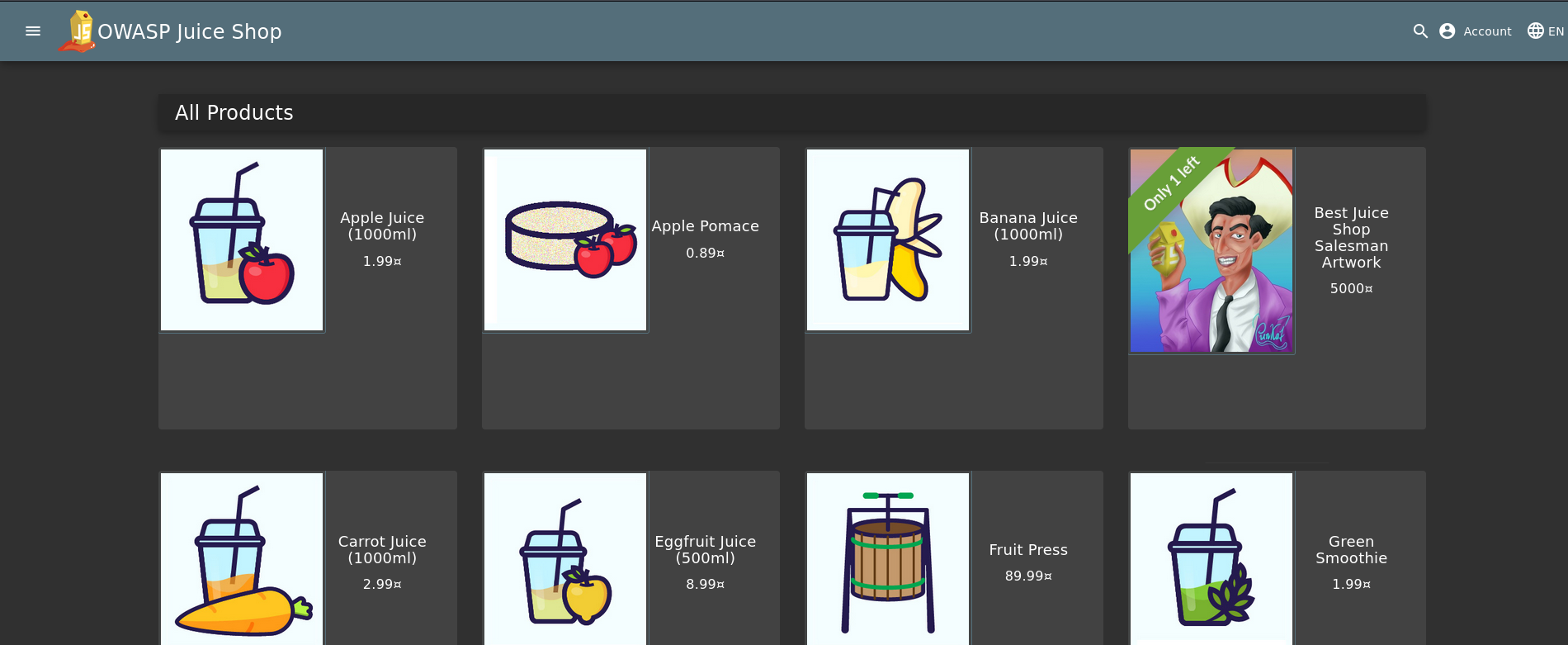
Inside that review? 💥 An email address.
Not just any email — an admin email.
⚠️ Pro Tip from the Icebox: Leaking emails in public-facing reviews is a terrible practice. Always sanitize your data before it gets displayed.
The Injection: Logging in Without Credentials
Now armed with an admin email, I headed to the login page.
Instead of brute-forcing passwords (too noisy and boring), I tested for SQL injection.
And guess what?
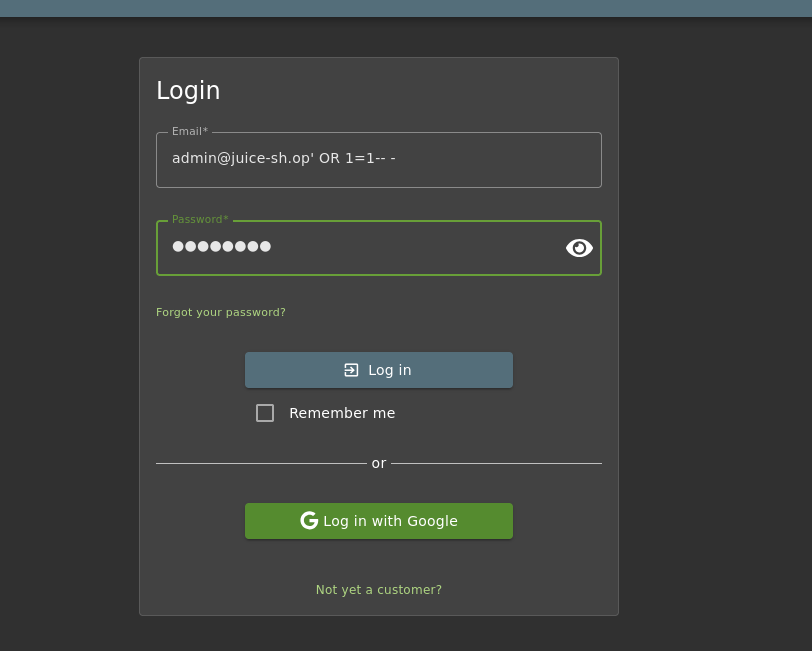
💀 It worked. I was in. Admin level.
No password required. Just a little ' OR '1'='1 magic.
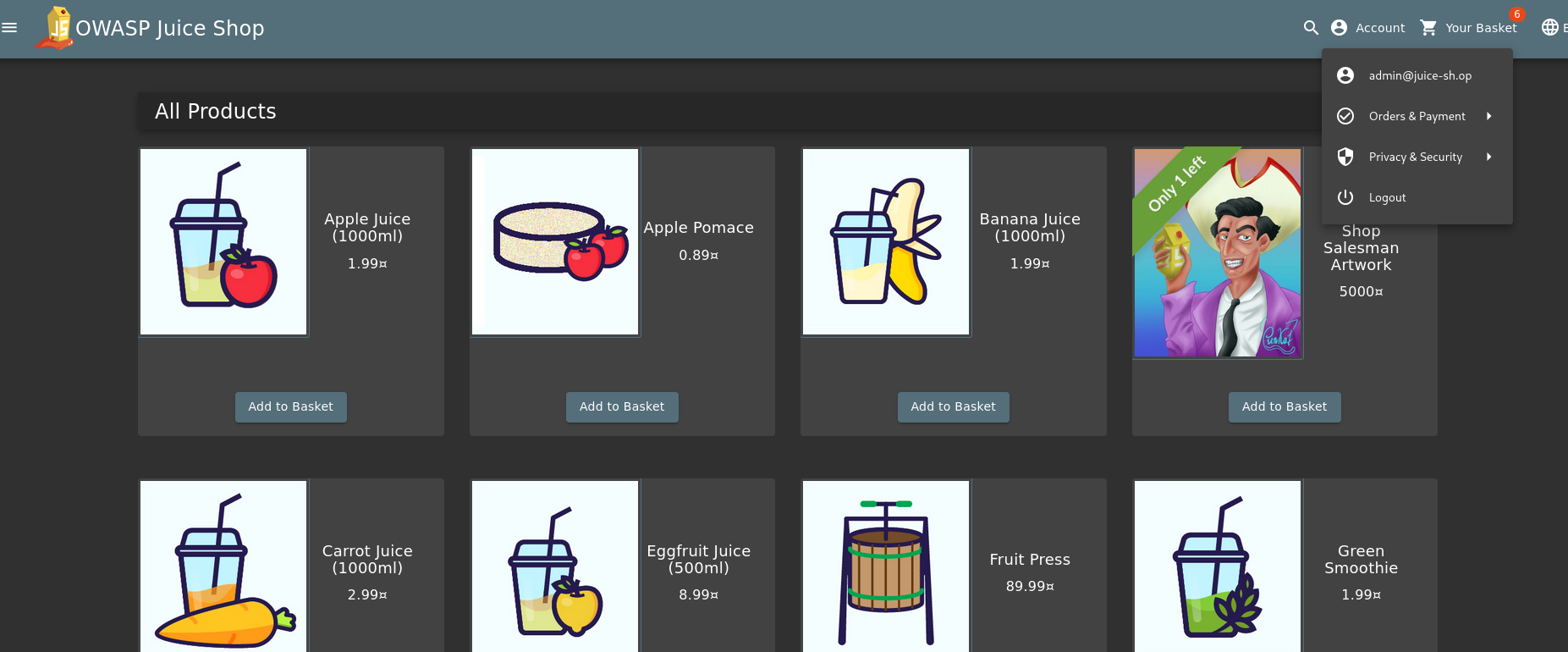
To confirm, I headed to the user profile page — and there it was: full access to the admin account.
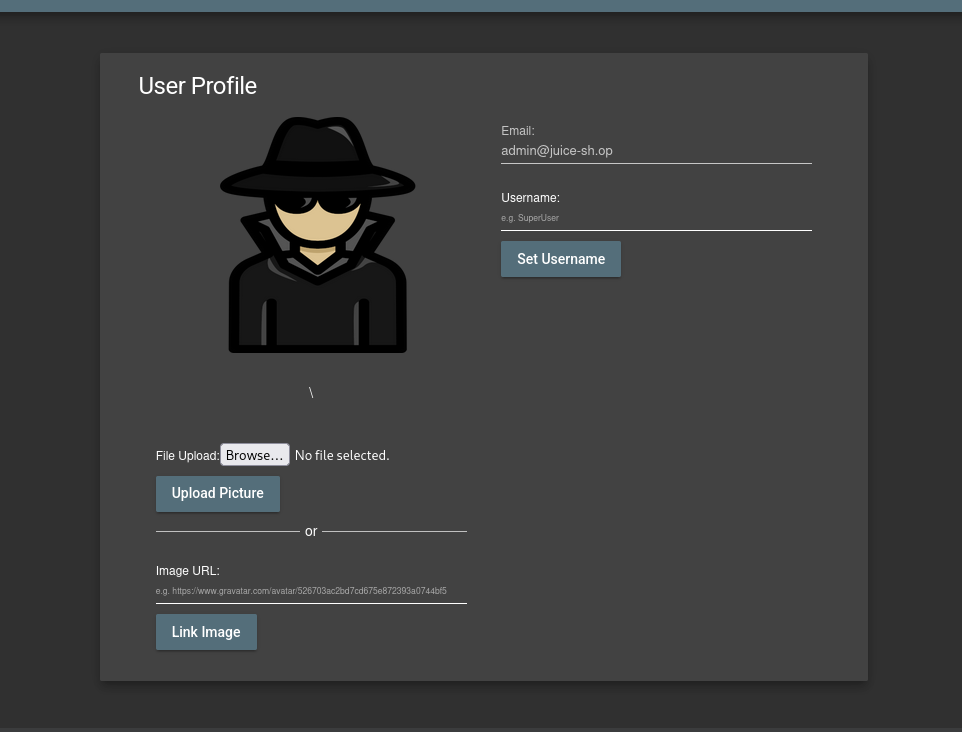
CVSS Analysis: How Bad Is This?
To measure the impact, I used a CVSS Calculator. This helps quantify the severity of a vulnerability and is essential for bug bounty hunting and responsible disclosure.
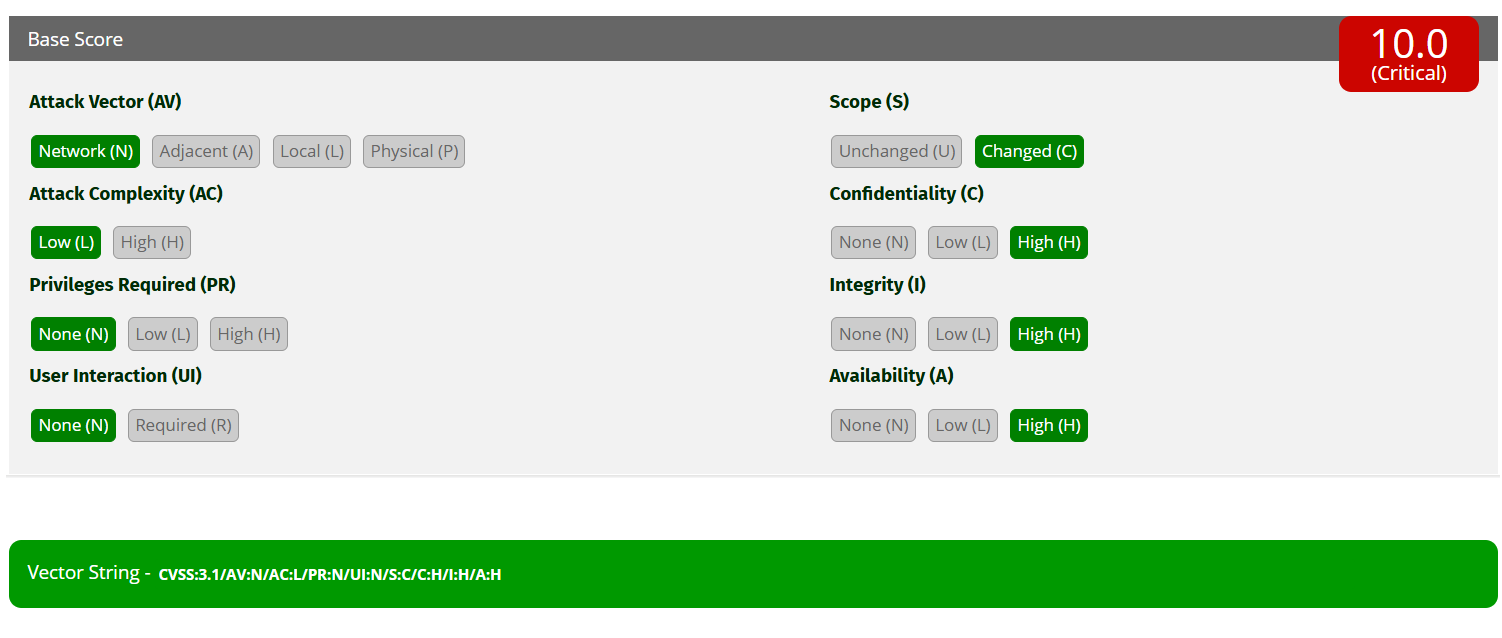
Let’s break it down:
| Metric | Value | Reason |
|---|---|---|
| Attack Vector | Network | Exploitable from anywhere in the world |
| Attack Complexity | Low | No tools or advanced setup needed |
| Privileges Required | None | We went from 0 to admin with no credentials |
| User Interaction | None | The attack did not require tricking any users |
| Scope | Changed | We accessed admin resources as a guest |
| Confidentiality Impact | High | Full access to user/admin data |
| Integrity Impact | High | We could modify or delete critical data |
| Availability Impact | High | Potential to disrupt app functionality |
Final Score: Critical
CVSS Vector String: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H“The colder the bypass, the higher the payout.” – Yeti ❄️
Why This Matters (and Why You Should Report It)
This kind of vulnerability is devastating for any organization. With admin access, you could:
- Read sensitive user data
- Tamper with system configs
- Wipe out logs or tracking data
- Deploy malware or persistence mechanisms
If this were a real-world app, this flaw could cost the company millions in damages. That’s why reporting high-severity bugs responsibly is not only the right thing — it's mission-critical for security teams.
Final Thoughts from the Icebox
This exercise showed how even one small misstep (like leaking an admin email) can be chained with a classic SQLi to crack open the whole system.
Bug bounty hunting is not about luck, it's about curiosity, persistence, and learning how things break.
"You don’t need an axe to break in — sometimes all it takes is a quote and an equal sign." – Yeti 🧠
See you next time with more cold-blooded hacks and frosty findings.
Yeti out. 🐾


