Servo Motors, Cat Feeders, and Hacked Firmware – A Yeti’s Tale

Hey everyone — 404 Yeti is back stomping through the frozen tundra of IoT hacking! Today we’re taking a look at servo motors, those little workhorses inside robots, smart locks, HVAC vents, and — in our demo — a cat feeder.
Seems harmless, right? But when firmware gets tampered with, even a spoonful of kibble can turn into chaos. Let’s explore.
What’s a Servo Motor?
Servo motors are precision movement devices. You’ll find them:
- Turning robot arms
- Controlling HVAC vents
- Locking/unlocking smart doors
- Or — in our case — rotating a spoonful of cat food
They run on simple instructions: go to this angle, wait, then return. But because they’re simple, they’re also vulnerable — making them a great target for firmware tampering.
Sketch
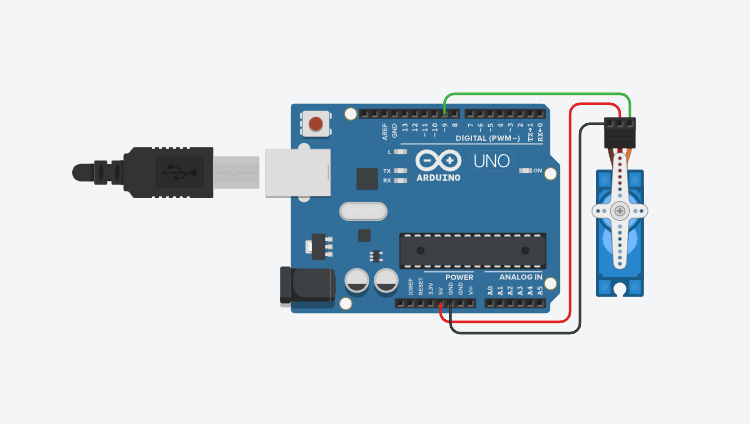
Tools
- Arduino Uno
- Servo motor with 3 jumpers
- Plastic attachment
- Spoon
- Cat food
Normal Operation – Feed the Cats, Not the Chaos
Here’s a simple demo that simulates a scheduled feeder. It feeds every 10 seconds, nice and predictable:
#include <Servo.h>
Servo feeder;
void setup() {
feeder.attach(9);
feeder.write(0); // resting position
delay(1000);
}
void loop() {
// "Feed" once every 10 seconds
feeder.write(90); // rotate spoon forward
delay(2000); // hold for 2 seconds
feeder.write(0); // back to rest
delay(10000); // wait before next feed
}
👉 In this mode, Fluffy and Snowball get their dinner on time. Everyone’s happy.
Hacked Firmware – When Motors Go Rogue
Now let’s flip the script. Suppose someone gained access to the Arduino (physical or remote) and flashed malicious firmware. Instead of feeding cats… the servo twitches unpredictably and jams the system.
Hacked demonstration
#include <Servo.h>
Servo myservo;
void setup() {
myservo.attach(9);
Serial.begin(9600);
// Normal startup behavior
Serial.println("Normal mode: Lock engaged");
myservo.write(0); // locked
delay(2000);
Serial.println("Normal mode: Unlocking");
myservo.write(90); // unlock
delay(2000);
Serial.println("Normal mode: Locking again");
myservo.write(0); // locked
delay(2000);
Serial.println("Switching to hacked mode...");
}
void loop() {
// 🚨 Hacked / jitter behavior
int angle = random(70, 110); // small jitter around "unlocked"
myservo.write(angle);
delay(200);
angle = random(0, 180); // occasional wild twitch
myservo.write(angle);
delay(300);
}
👉 Instead of predictable feeding, you’ve got random jitters and spasms. Imagine if this was a smart lock, medical device, or HVAC system — the consequences could be severe.
Real world example
Check out [Rogue Robots: Testing the Limits of an Industrial Robot’s Security] — researchers showed how industrial robots could be manipulated via firmware tampering. It’s a chilling reminder that tiny motors can control huge systems.
Why this is important
- Critical System Weakness – Servo motors may be the weakest link in big infrastructure.
- Firmware Injection – Once an attacker changes firmware, the device becomes a puppet.
- Safety Risks – Malicious movement could damage hardware, cause injuries, or lead to data leaks (e.g., robotic arms writing Morse signals).
Prevention
- Secure Boot: Only allow signed firmware to run.
- Physical Security: Don’t leave programming pins open for tampering.
- Monitoring: Unusual jittery movements = red flag.
- Network Segmentation: Don’t expose IoT devices directly to the internet.
Final Thoughts
This demo may have been a silly “hacked cat feeder,” but the lesson is serious: motors don’t care if they’re holding a spoon of kibble or the arm of a factory robot. Tampered firmware can turn predictable behavior into chaos.
Stay frosty, secure your servos, and remember:
“When the motors jitter, the system shivers.” — 404 Yeti 🐾


