Reverse Engineering TP Link TL-WR841N V14.80 firmware

Hey everyone — 404Yeti here. Today we’re going on a little IoT archaeology trip: enumerating a TP-Link router, sniffing boot signals, and peeking into its firmware to understand what secrets live inside. This is an educational exercise in firmware analysis and defensive research — don’t poke devices you don’t own. Let’s go melt some ice.
OSINT
First stop: the hardware label. If the device has an FCC ID (or similar regulatory IDs), note it — that’s a goldmine. The FCC database and vendor pages often contain:

Next lets go to fcc id website and see if we can find some information
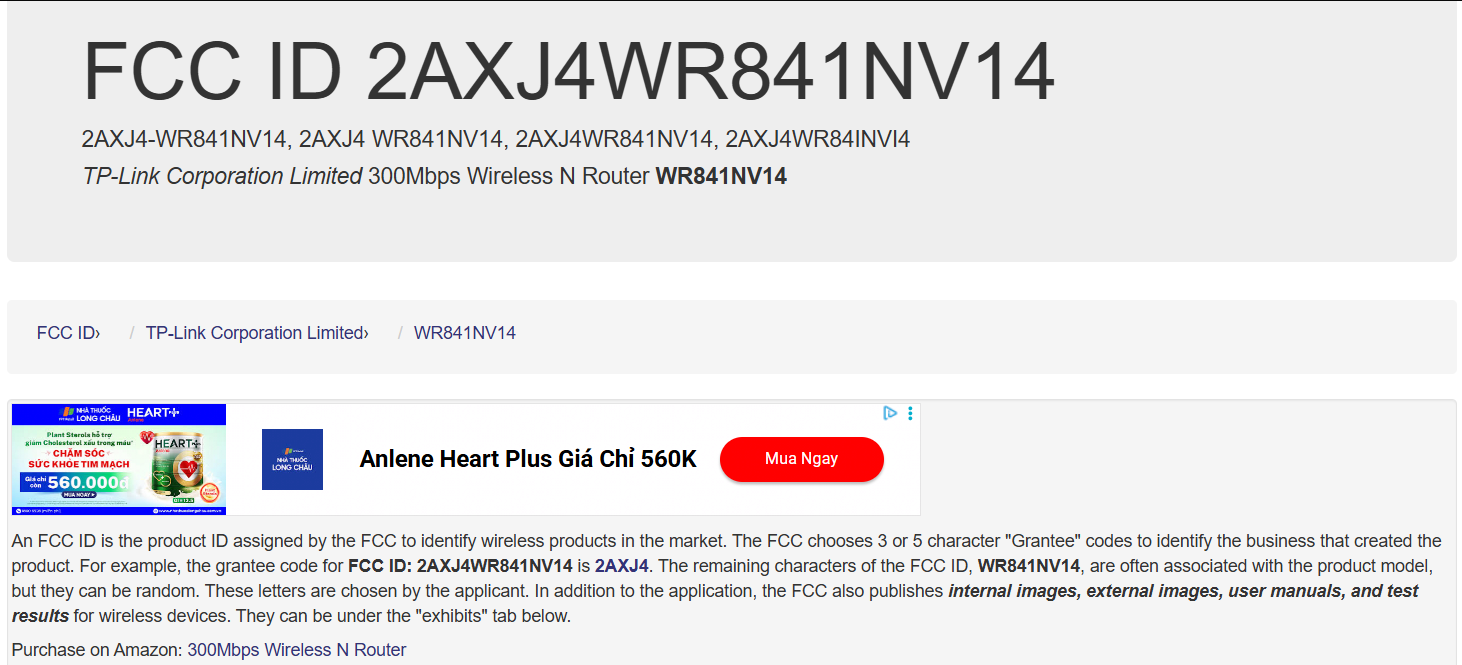
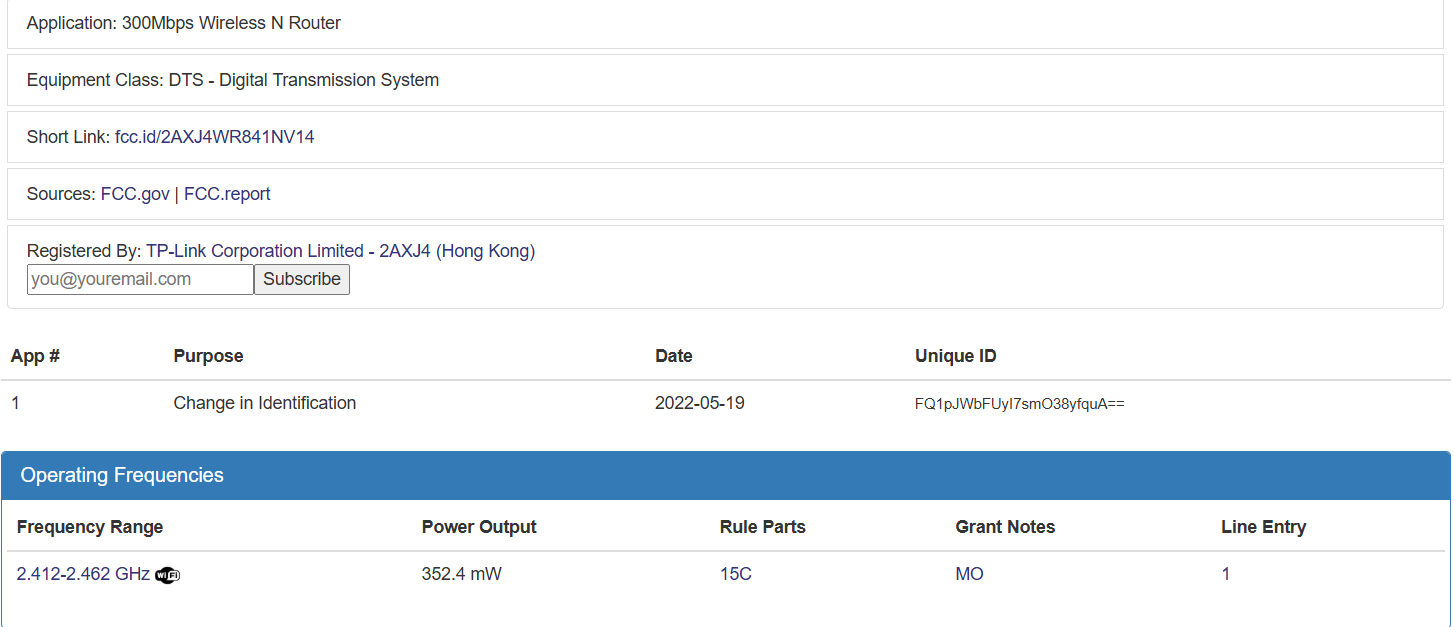
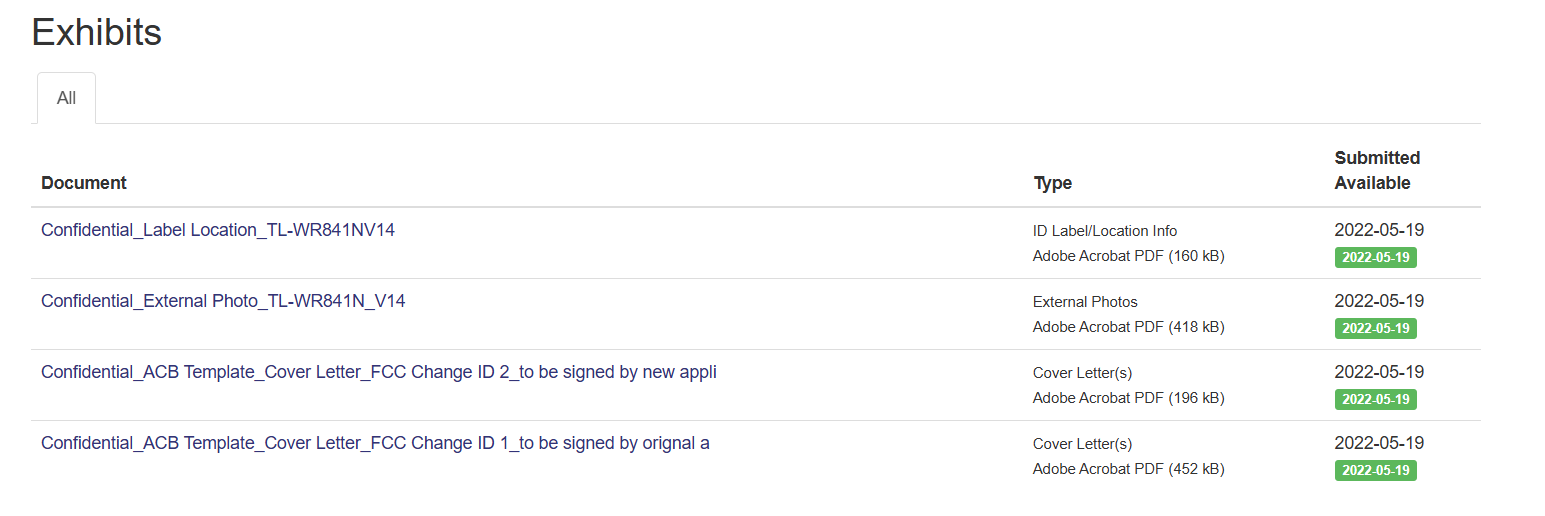


As you can see we are provided with some very juicy information! This website provides alot of information from diagrams to actual component pictures which can come in handy!
Logic Analyzer / UART
Now that we have completed our osint enumeration lets pivot over to some logic analyzer capture
Logic Analyzer
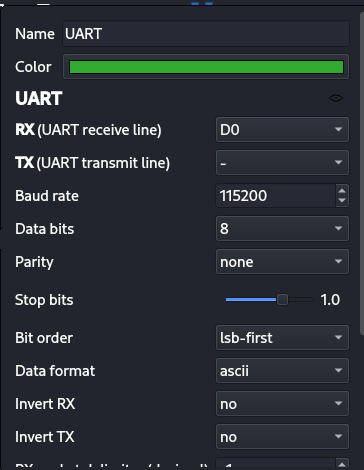
Next, capture the router’s boot. Attach a logic analyzer or UART adapter to the serial pins, power the device, and record the first 10–20 seconds of boot. In tools like PulseView you’ll see waveforms — those are the device talking.
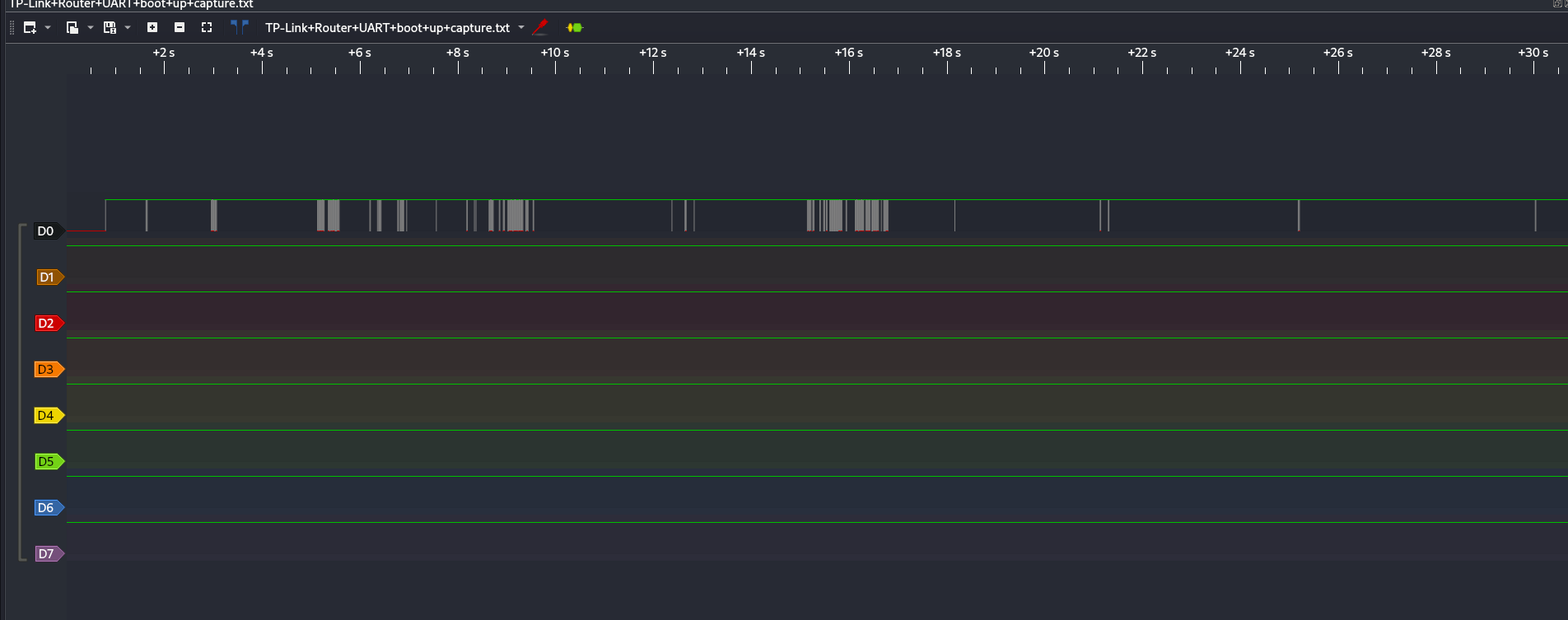
- Add a UART decoder in the tool and configure it for the usual serial parameters (baud/parity/stop bits).
Switch output to ASCII (not hex) to read human-friendly boot logs.
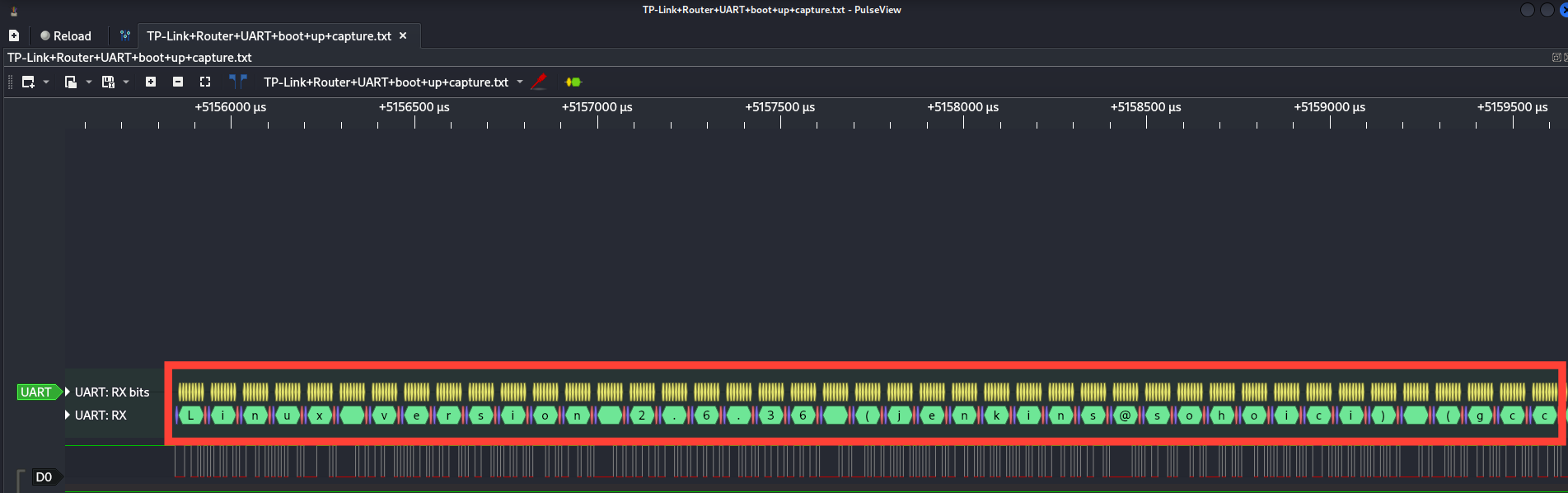
now we can see some information. In our case we can see this is linux version 2.6.36 Good find!
Get the Firmware
If you can’t physically dump the flash, pull the firmware image from the manufacturer’s support site. Vendors often publish firmware for updates — perfect for offline analysis.
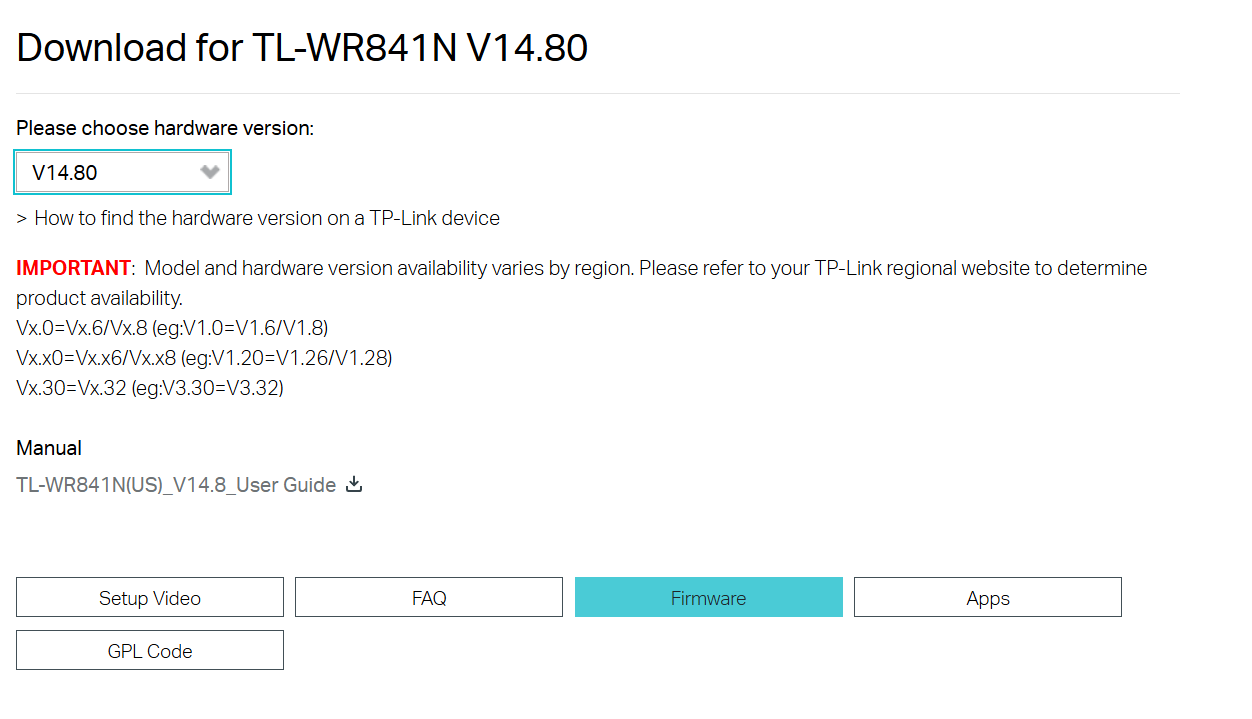
After download we should run strings to make sure we can see some quick information on it.
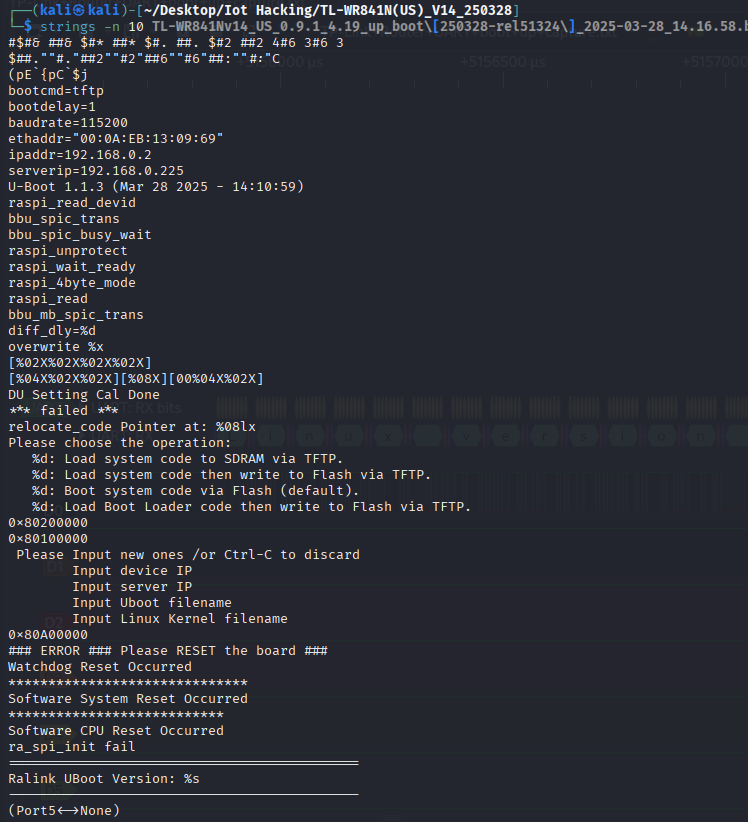
fortunately nothing is scrambled so we can search for some info if you want.
Next lets do binwalk enumerate the binaries.
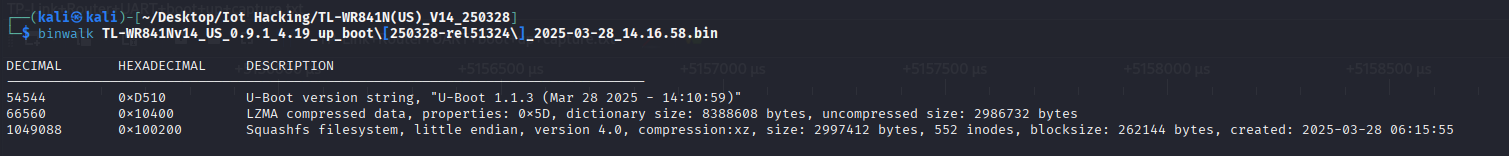
we now have useful information about the type of binaries we are dealing with and what information we could receive.
Next lets check for entropy to see if there is any encrypted information.
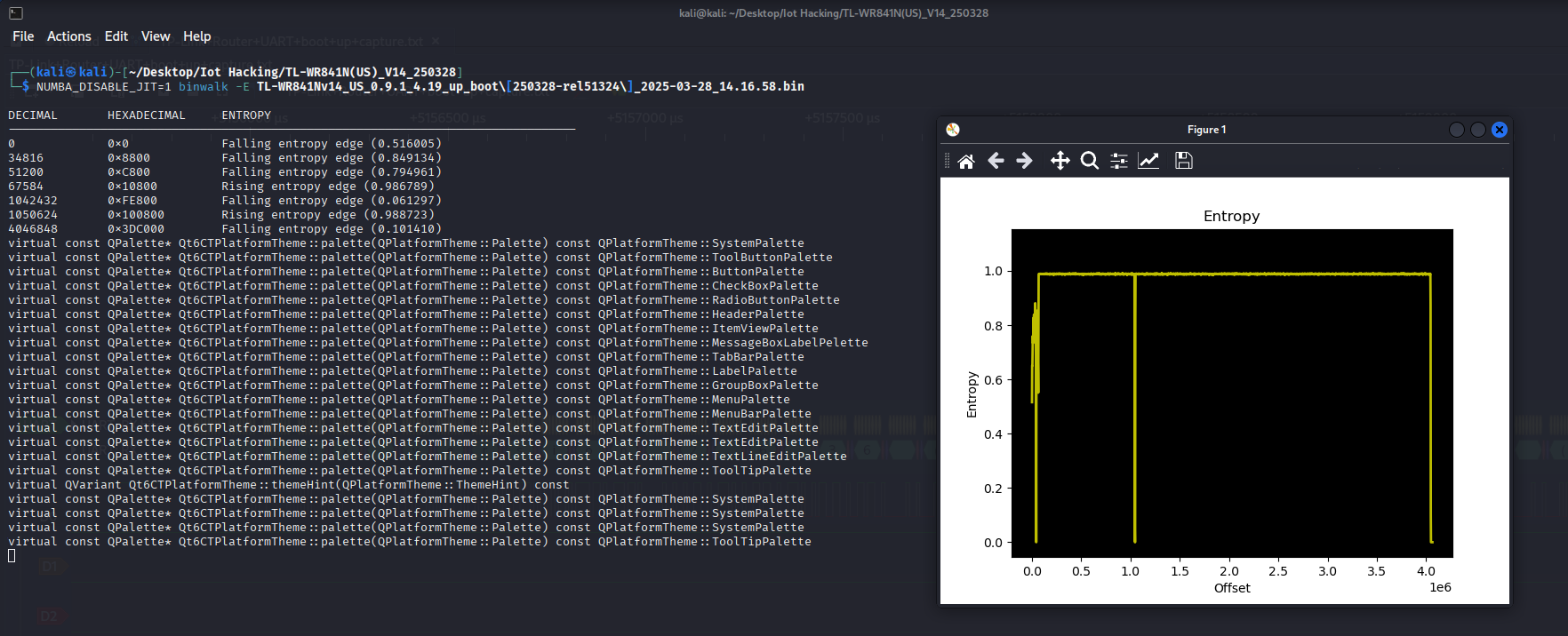
we can see quite a few sections are at 1 which means they encrypted!
Now we need to extract the binary
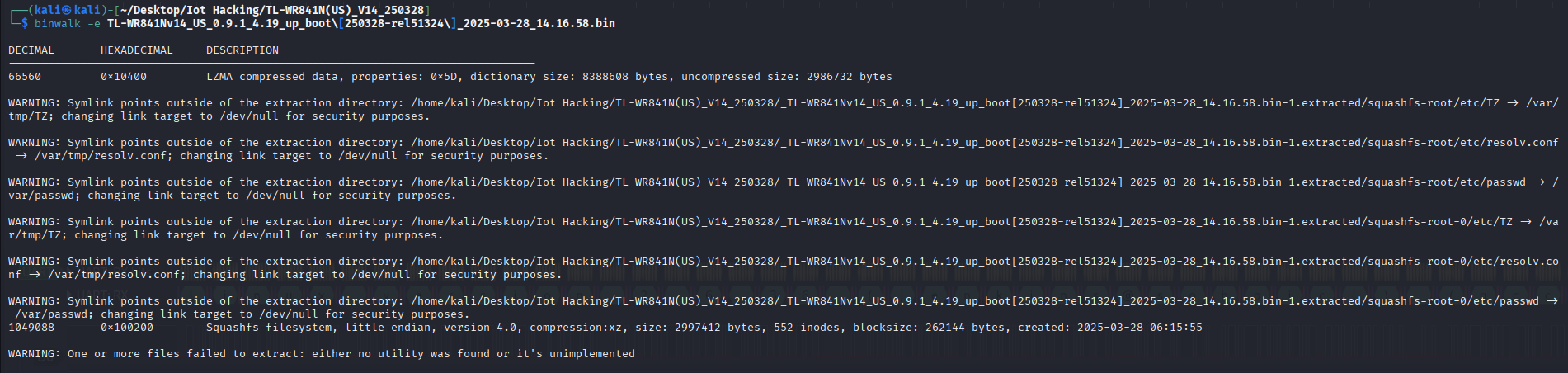
looks like a successful pull
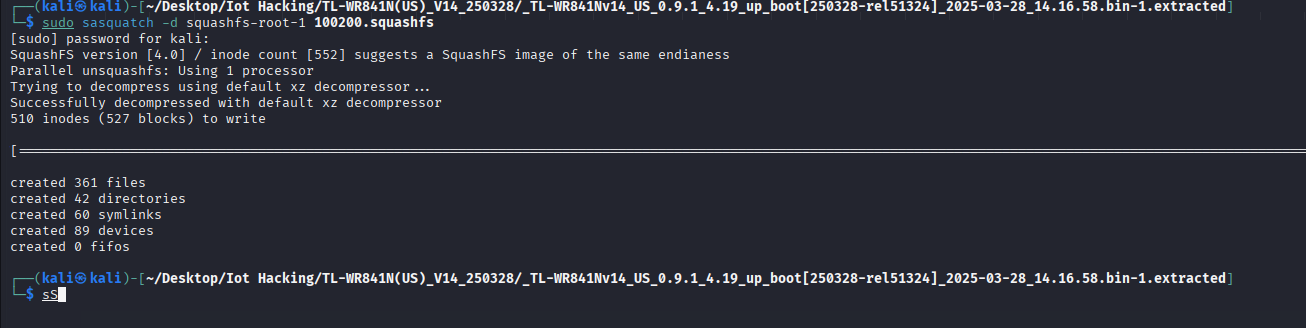
Next lets decompress the binary with sasquatch
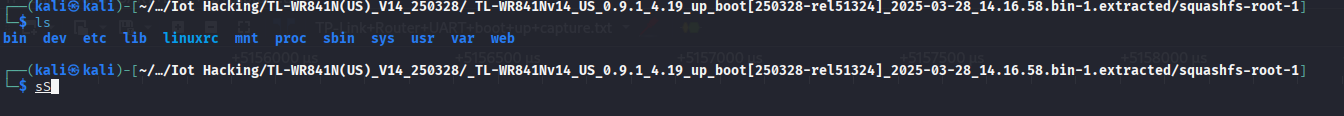
now we can see we can access this information
Carve the Filesystem
we need to go back and carve out a file system that was not done for us which is for U-Boot
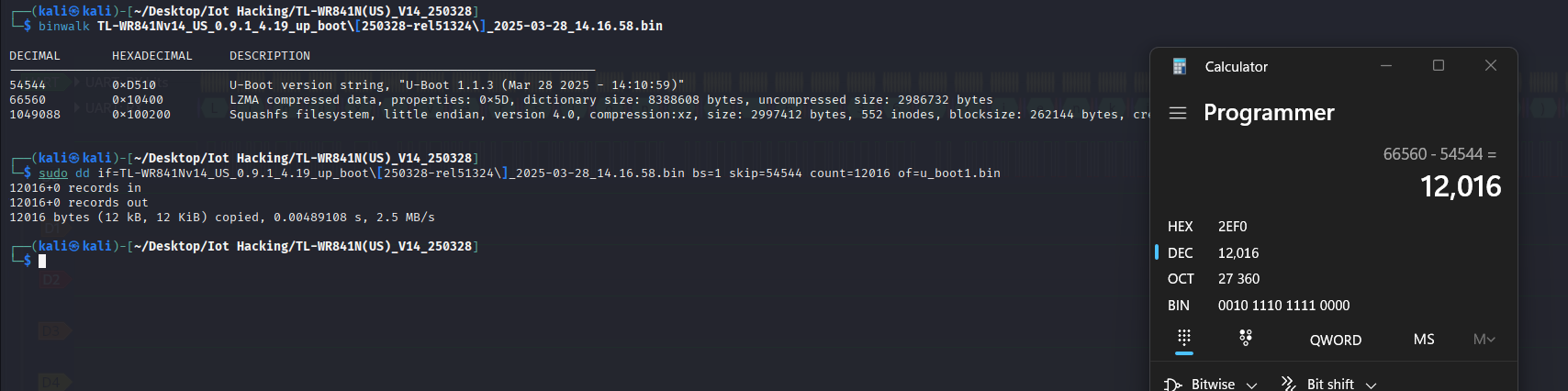
for us we need to do some math we can find the difference between lzm4 and u-boot
do strings for a sanity check
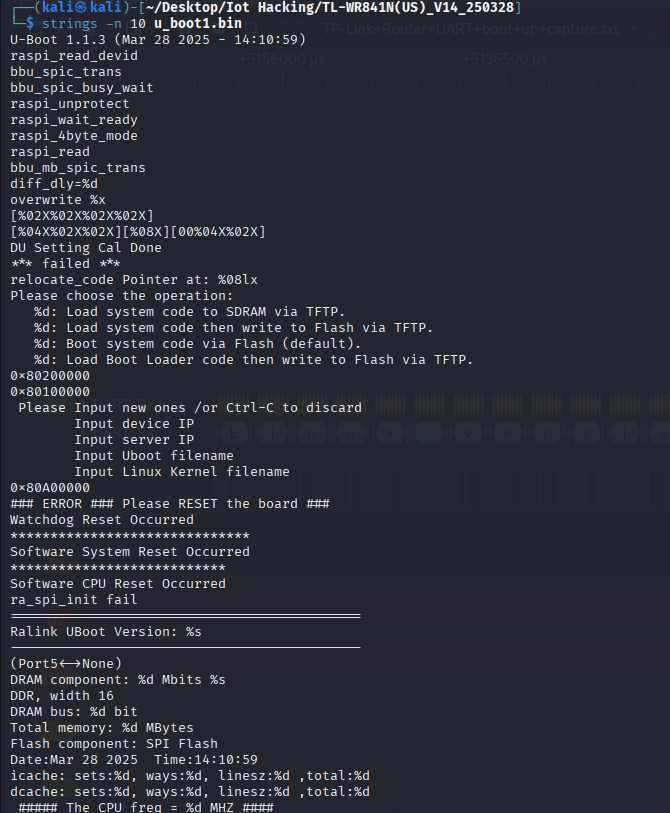
next lets enumerate the file system for any .xml files
lets test if we can cat out the the config xml file
we see a bunch of junk so we need to decrypt it. So lets find where we need locate these files
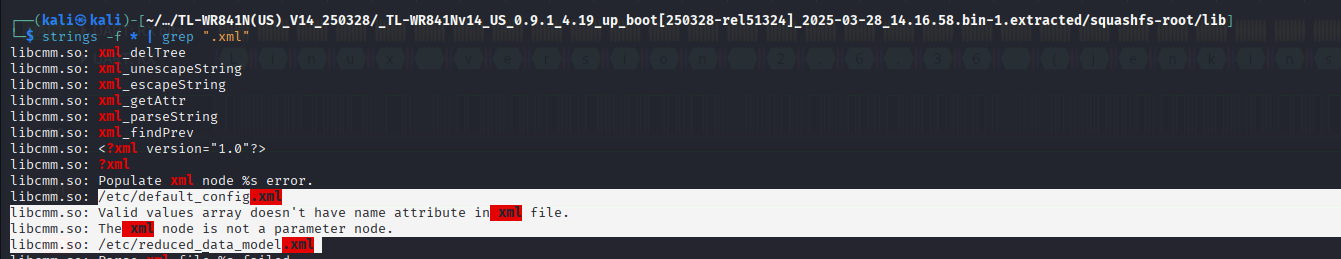
Reverse Engineering
If you find a binary routine that looks like decryption, load it into a disassembler/RE tool and search for likely function names (e.g., decrypt, dm_decryptFile, or other vendor-named helpers). The goal is to:
- Identify the decryption routine and algorithm (AES, XOR, custom)
- Find where keys are stored or referenced (sometimes hardcoded, sometimes derived)
- Understand how encrypted blobs are processed (padding, IV usage)
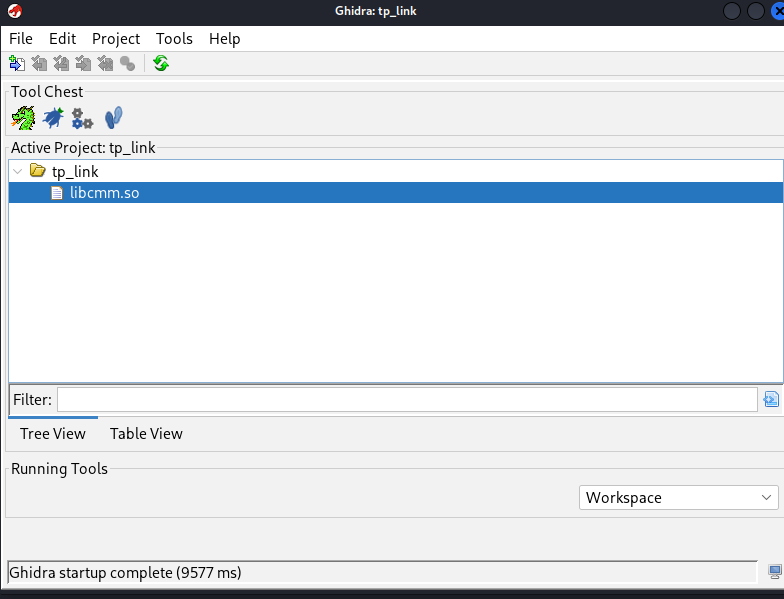
so lets look for something like "decrypt" in the search section
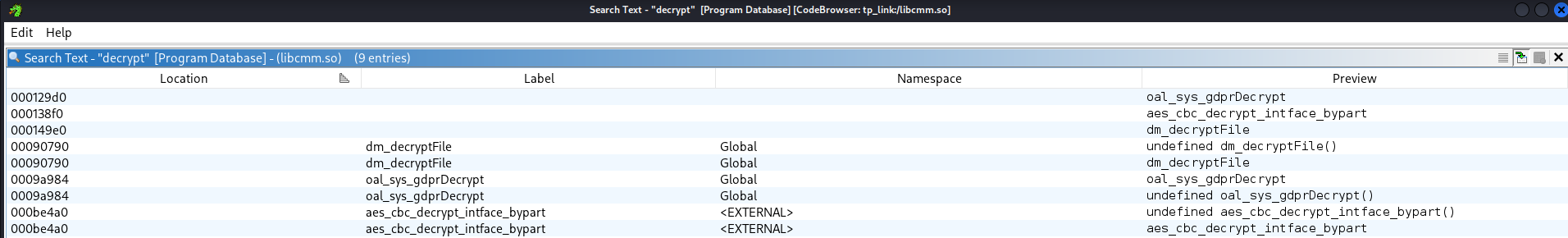
now we see two files called "dm_decryptFile" lets look at them and see if find anything interesting.
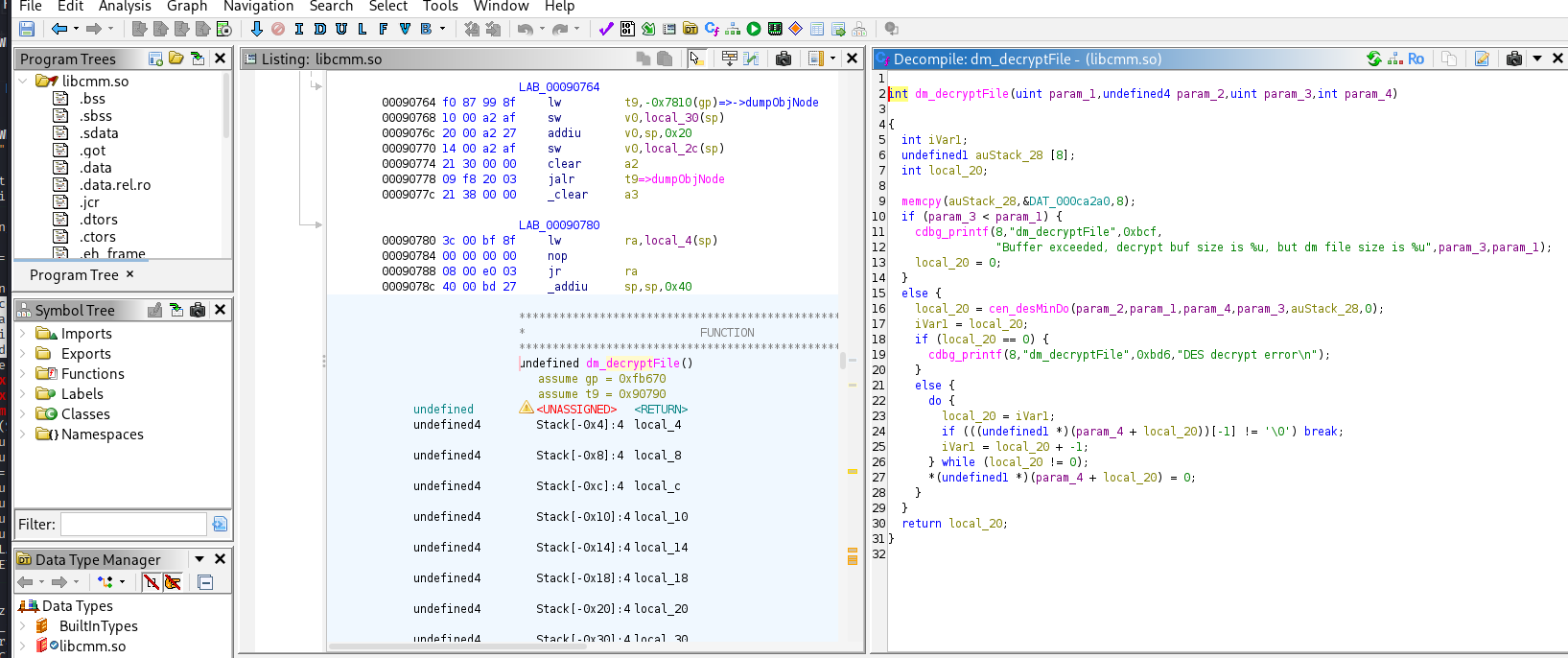
now we can see some reversed information from assembly to C.
we noticed that this DAT function seems to be something of interesting so lets see if we can follow it
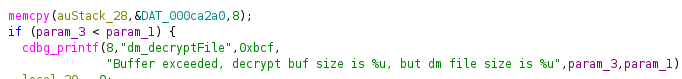
when we step into it with ghirda we see a special set of characters
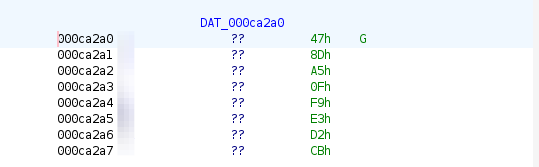
we see that this looks like a cipher key. so we should try to see if this can be used for something.
So lets make a copy of the config file xml and we will try to use a tool called openssl to see if we use this cipher key.
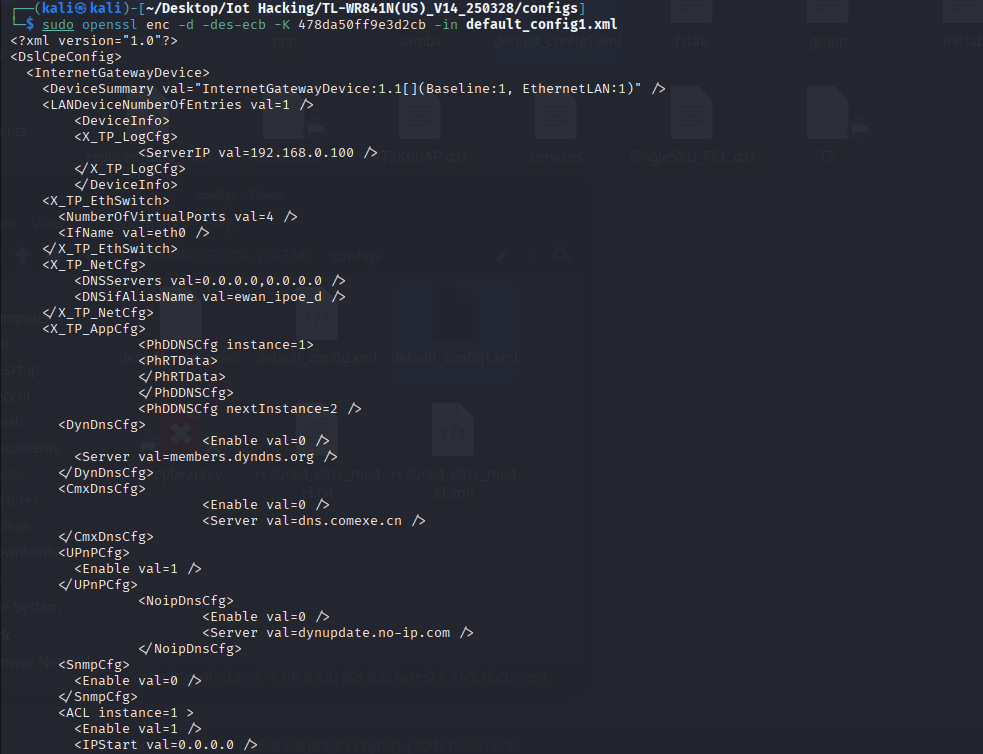
now we see we have decrypted the configs file. lets see if we can find anything juicy
unfortunately we didn't get everything right the first time. it is showing that we have some padding so maybe we need to run openssl with no padding
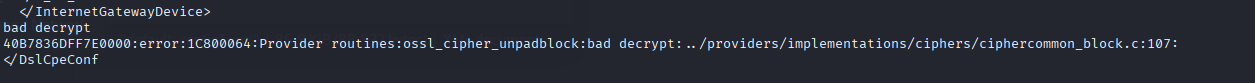
lets try again with the -nopad flag
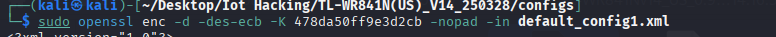
great no problem now we have a clean read.
next lets do our next file which is the reduced_data_model.xml
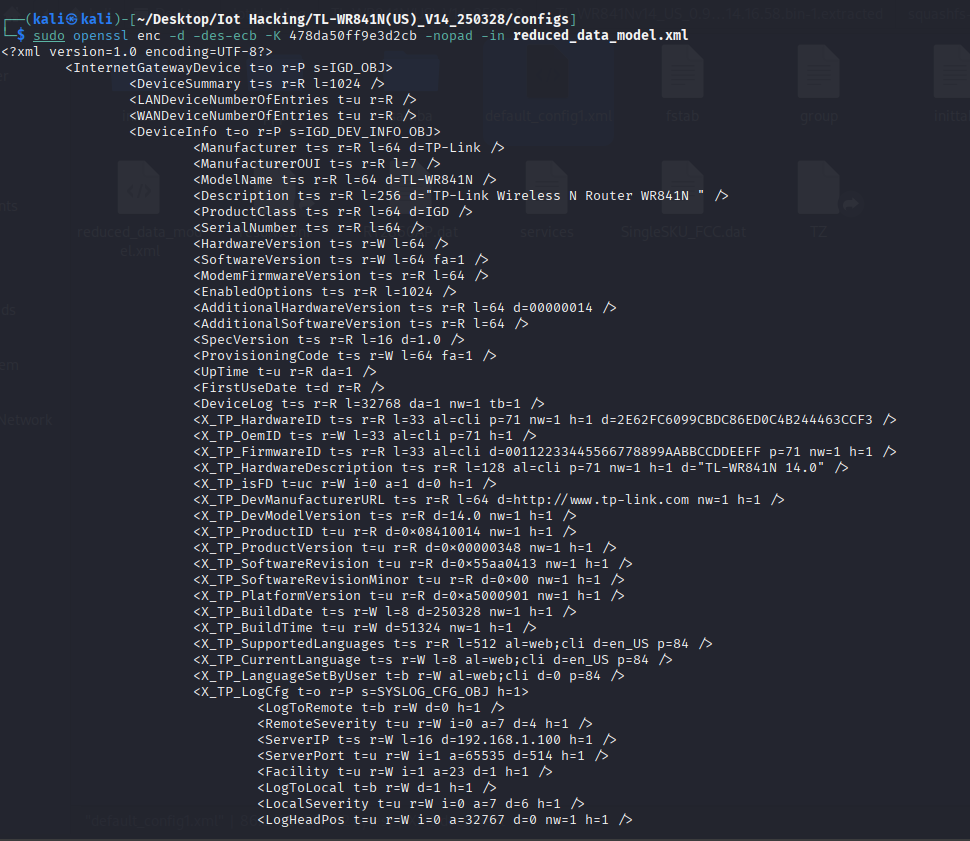
this time we do see something juicy
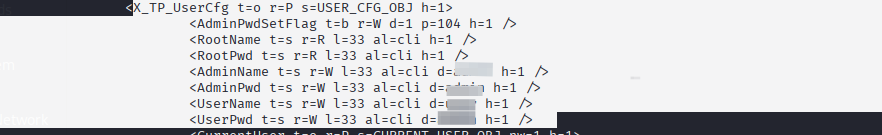
we have default credentials for this router now. This is normal for routers. But this is highly dangerous because no one changes these default credentials so if someone wanted access to your router they could and start to cause problems on your home network.
Why This Matters
- Default credentials and exposed config files make it trivial for attackers to take over home or small-office routers if remote access is poorly controlled.
- Hardcoded keys or weak encryption in firmware mean attacker with a firmware image (or device access) can decrypt sensitive config material.
- Legacy bootloaders & old kernels present known vulnerabilities and unpatched attack surfaces.
- Compromised routers can be pivot points into internal networks, beacons in botnets, or DNS hijack platforms.
How to fix it
- Change default admin passwords immediately.
- Disable remote admin and UPnP if not required.
- Keep router firmware up to date and subscribe to vendor advisories.
- Segment IoT devices away from sensitive networks (VLANs).
- Monitor router behavior and logs for anomalies (unexpected DNS changes, outgoing connections).
Final thoughts
Firmware analysis is like digging through a frozen glacier: the surface reveals structure, but the real treasure (and danger) lies in the layers beneath. Routers, in particular, are a sweet spot — widely deployed, often poorly maintained, and full of default settings that invite abuse.
“If a device speaks, listen — but don’t shout. Find the problem, tell the owner, and patch the hole.” — 404Yeti 🐾


