🧊 Directory Busting in OWASP Juice Shop with FFUF: Yeti Digs Deep

Heyo snowpackers — Yeti here, fresh off the slopes and armed with a fuzz cannon.
Today, we’re smashing down snow-covered doors in the world of directory busting — one of the oldest recon tactics that still lands juicy bugs (and bounty bucks). Let’s melt some ice with FFUF and OWASP Juice Shop. 🧨❄️
What is Directory Busting?
Directory busting (also known as path or endpoint fuzzing) is like treasure hunting with a battering ram. We're slamming our way into hidden URLs and undocumented routes that the developers hoped you wouldn’t find — but the Yeti always finds.
These routes might look like:
/admin/backup/api/debug/ftp/hidden-flag
“Security through obscurity is like hiding honey from a bear by putting it under a blanket.”
— Yeti, probably
Why does this matter?
These forgotten or "secret" directories often expose:
- Unprotected admin panels
- Sensitive configurations
- Backup files
- Internal API endpoints
- Entry points for further exploitation.
Let’s Fuzz with FFUF
Once you’ve spun up your Juice Shop at http://localhost:3000, it’s time to drop some FFUF fury:
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://localhost:3000/FUZZBreakdown:
| Flag | Meaning |
|---|---|
-w | Wordlist (e.g., from SecLists, DirBuster, etc.) |
FUZZ | Placeholder that FFUF replaces with each word |
-u | Target URL + injection point |
-fs 80117 | Filters out boring 404 pages (Juice Shop returns 80117-byte 404s) |
-o | Output saved to a file for easy digging later |
Bonus Tip: You can also fuzz subdirectories like/upload/or/api/to go deeper:
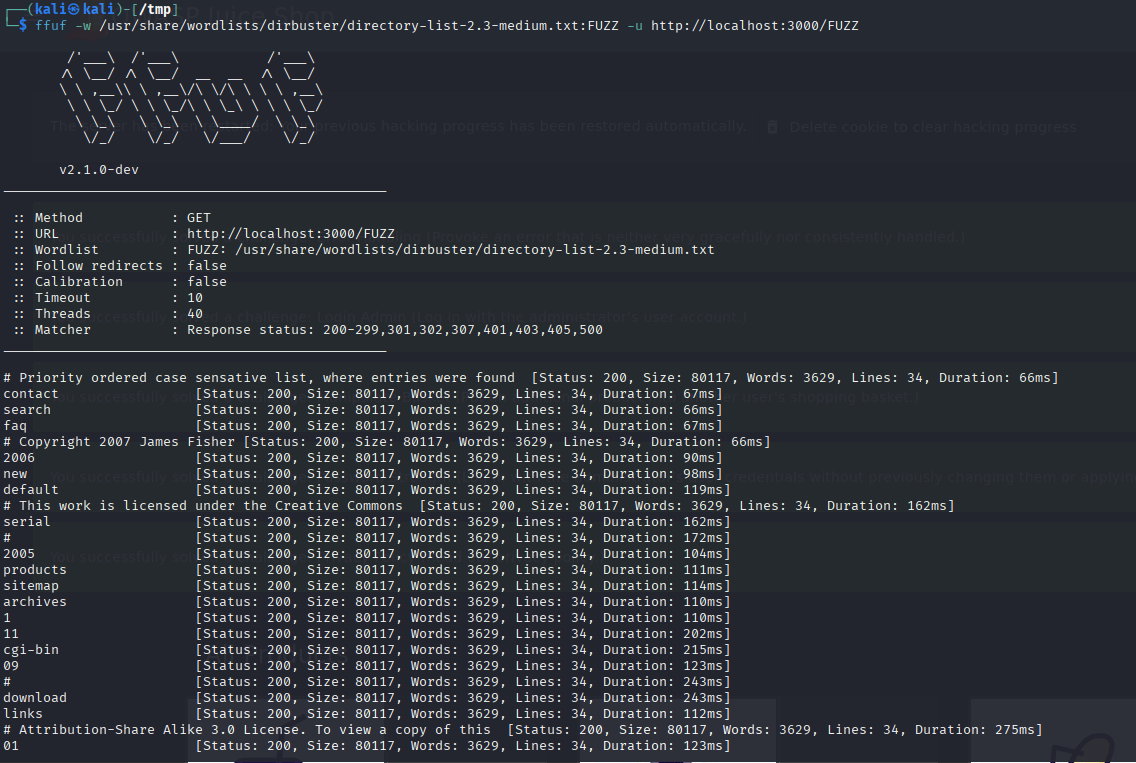
here we can see a common file size so maybe we can add the filter -fs to ignore a common file size. in our case 80117 So lets update our command but because there might be a large amount of endpoints lets make sure we save this to a file. So we will add > juicedir.txt so we will be saving all our endpoints to this file.
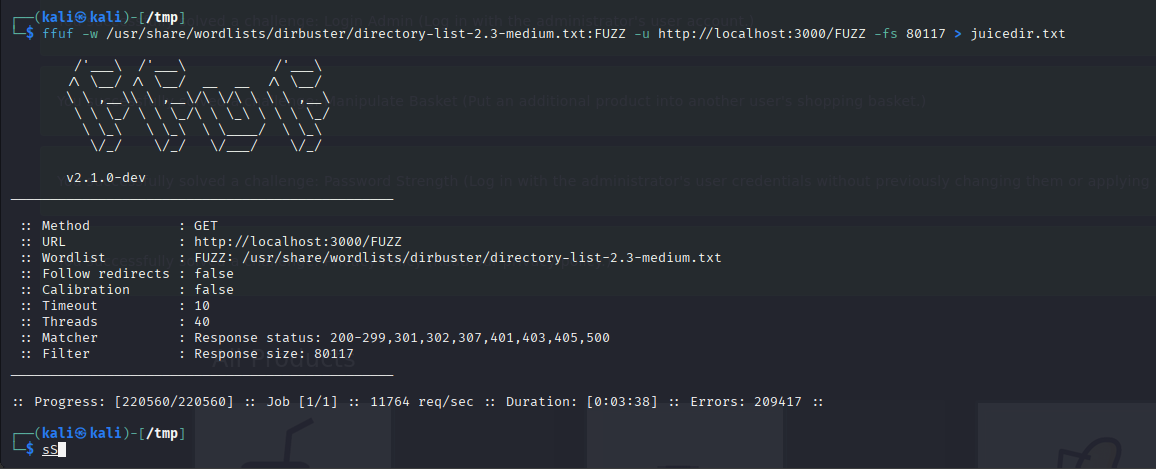
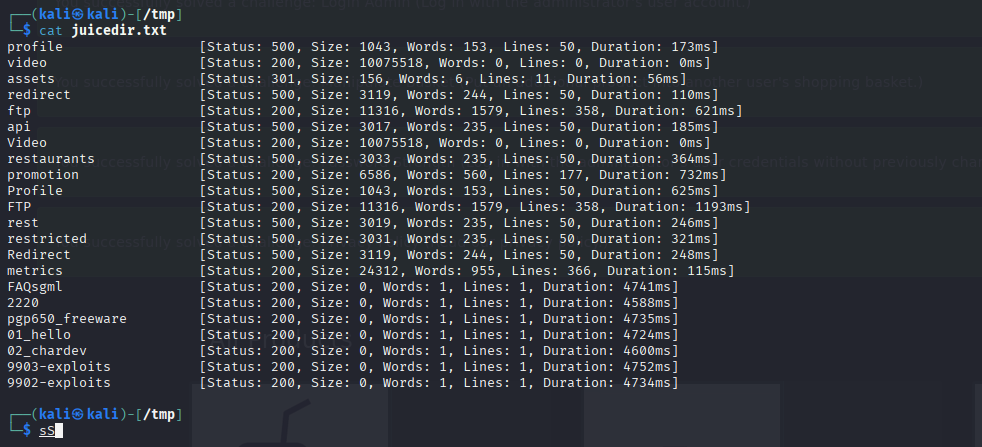
so next we can check what endpoints are available by using cat which allows you to read a file on the terminal and we can see quite a few endpoints
Sample Win: Hitting Gold
Let’s say one of the results is:
localhost:3000/ftp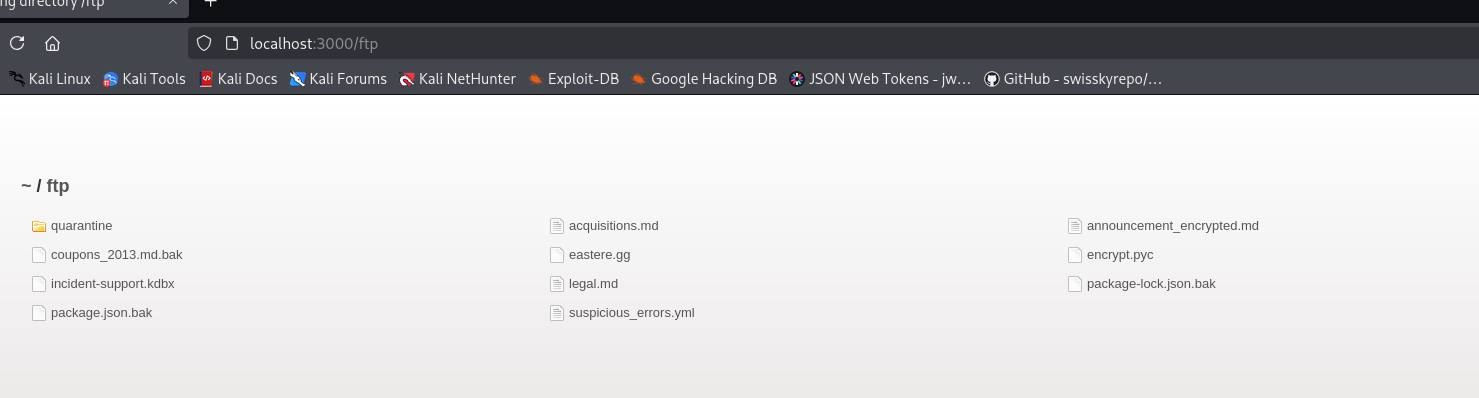
Click it.
Suddenly you’re inside an internal file browser...
Configs, server logs, user exports — all staring back at you.
That’s no longer just recon — you’ve pivoted into information disclosure, privilege escalation, or even remote code execution depending on what’s exposed.
Real-World Impact: This Ain’t Just a Toy Problem
Too many devs think "If no one links to it, no one will find it."
That’s how backup files (.bak, .zip, .env) and dev panels leak out onto production servers.
So let's score this using CVSS v3.1, assuming you found a juicy unprotected endpoint like /ftp or /backup.
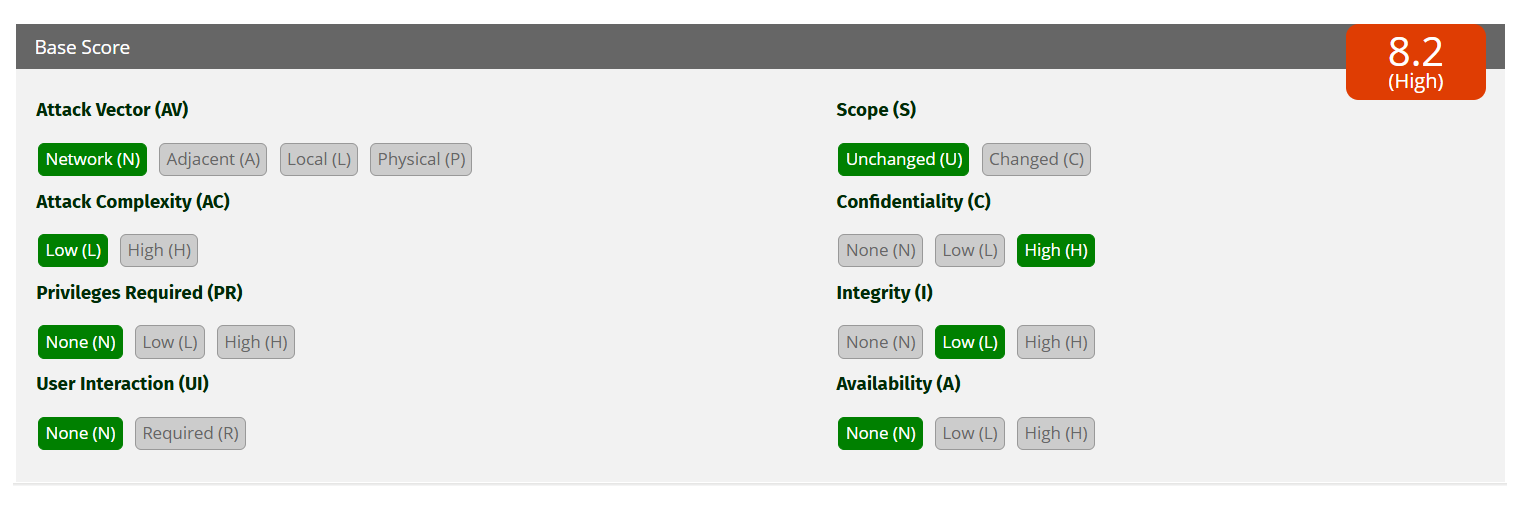
| Metric | Value | Why |
|---|---|---|
| Attack Vector | Network (N) | Anyone can access it remotely |
| Attack Complexity | Low (L) | No special conditions needed |
| Privileges Required | None (N) | Publicly accessible |
| User Interaction | None (N) | No clicks or triggers needed |
| Scope | Unchanged (U) | Still inside original system boundary |
| Confidentiality | High (H) | Could leak sensitive data, source code, secrets |
| Integrity | Low (L) | Might be able to alter minor content |
| Availability | None (N) | Doesn’t crash or disrupt service |
Final CVSS Score: 8.2 – High
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N
"Sometimes the most dangerous doors are the ones no one remembers building."
— Yeti, breaking into/forgotten-admin
Pro Tips from the Iceberg
- Use a Custom Wordlist: Tailor your list to the tech stack. PHP apps? Try
.php,.bak,.zip. Node.js? Hitdebug,env,test. - Recursive Enumeration: Found
/upload/? Fuzz inside it. Found/admin/? Fuzz that for more gold. - Filter Smart: Use
-fc,-fs, or-mcto ignore noise and hone in on the juicy stuff. - Log Everything: FFUF logs are gold for reporting, auditing, and building repeatable methodologies.
Summary
Directory busting isn’t flashy. But it works.
It’s one of the easiest ways to go from 0 to critical in minutes — especially when developers leave things lying around like exposed flags and misconfigured endpoints.
One well-placed FFUF run can uncover:
- Broken access control
- Public backups
- Forgotten debug APIs
- Sensitive user data
- Initial footholds for full compromise
Final Yeti Wisdom
“Every app has a skeleton closet — and I’m here to rattle the bones.”
— Yeti, the Arctic App Breaker
That’s it for this frosty session.
Keep fuzzin’, stay sneaky, and always:
✅ Respect the scope
✅ Keep it legal
✅ Report responsibly
Until next time — Yeti out. 🐾☃️