Cracking Signals with PulseView – SIGINT Yeti Style

⚠️This was an educational learning experience, no live signals were harmed(captured) in the making of the blog⚠️
Hey snow scouts, 404Yeti is back, and today we’re doing some good old-fashioned Signal Intelligence (SIGINT) — this time ripping into a capture from a wireless router and digging out a hidden flag. ❄️🐾
What is Sigint?
SIGINT (Signal Intelligence) is the art of capturing and analyzing signals from devices. In the world of IoT and wireless gadgets, these signals are like footprints in the snow — if you know how to read them, you can reconstruct the trail.
Think:
- Smartwatches pinging phones
- Routers beaconing out Wi-Fi management frames
- BLE devices spamming advertisements
- Even satellites whispering data streams down to Earth
For us hackers-in-training, SIGINT is about turning noise into knowledge
Walkthrough
- Load the Capture in PulseView
Fire up PulseView and load your capture file.
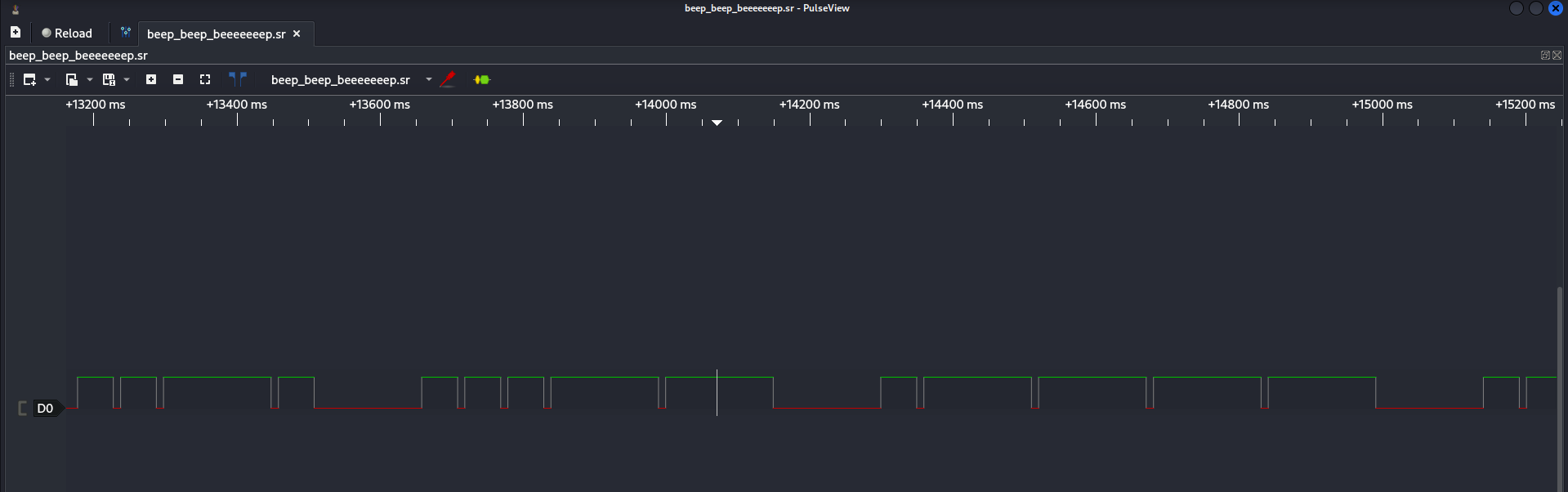
You’ll see a waveform of bits and pulses — the raw language of the machine. Looks messy at first, but there’s always a pattern.
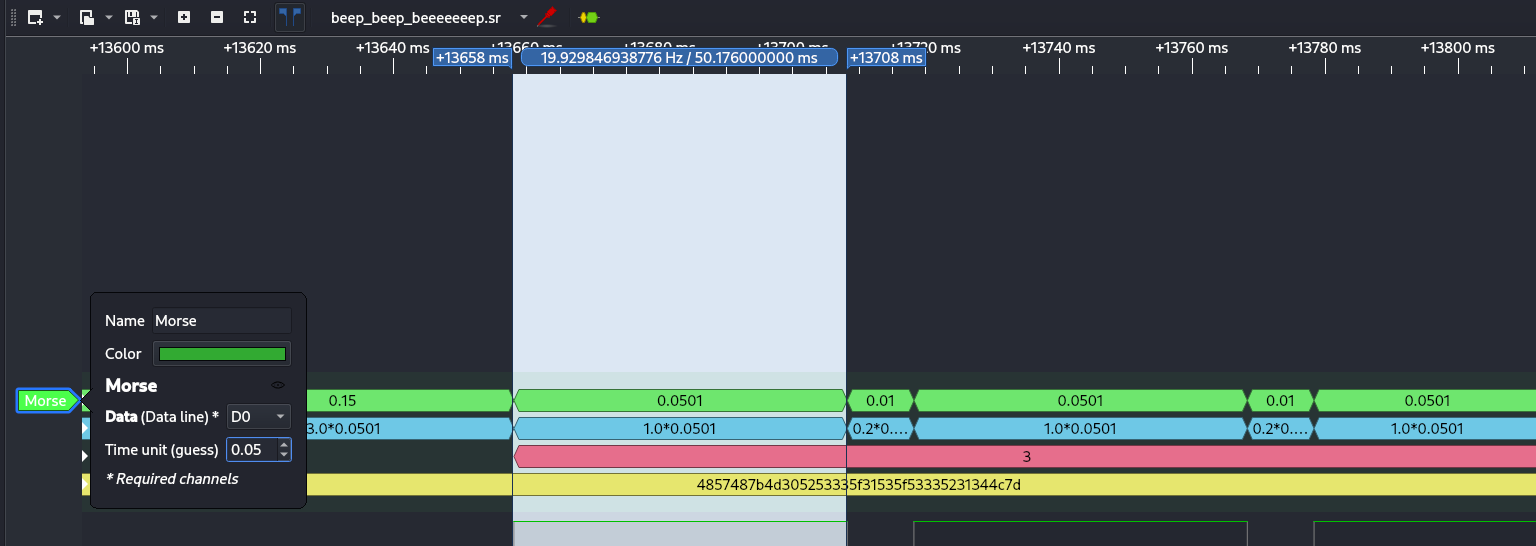
- Add a Morse Decoder
PulseView has protocol decoders. Add a Morse decoder, feed it the channel, and set your timing:
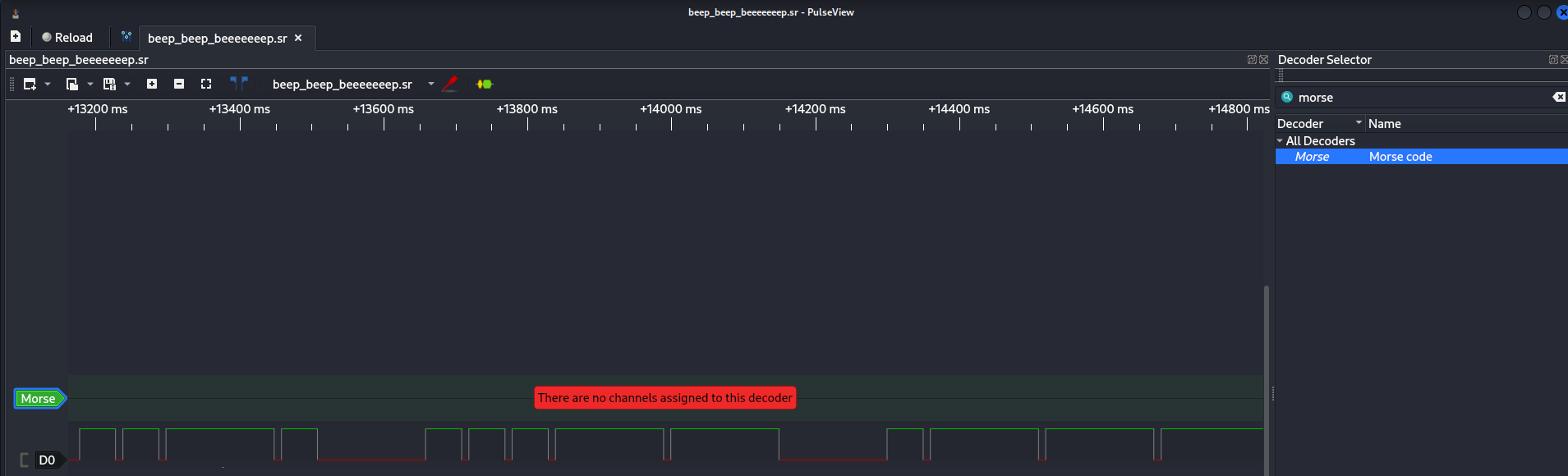
Make sure to add the right data which D0
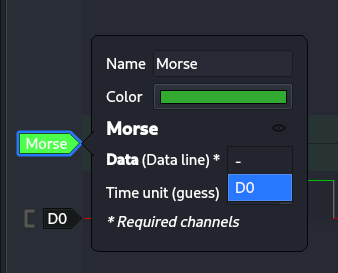
Change the frequency to ≈ 0.05 (50ms)
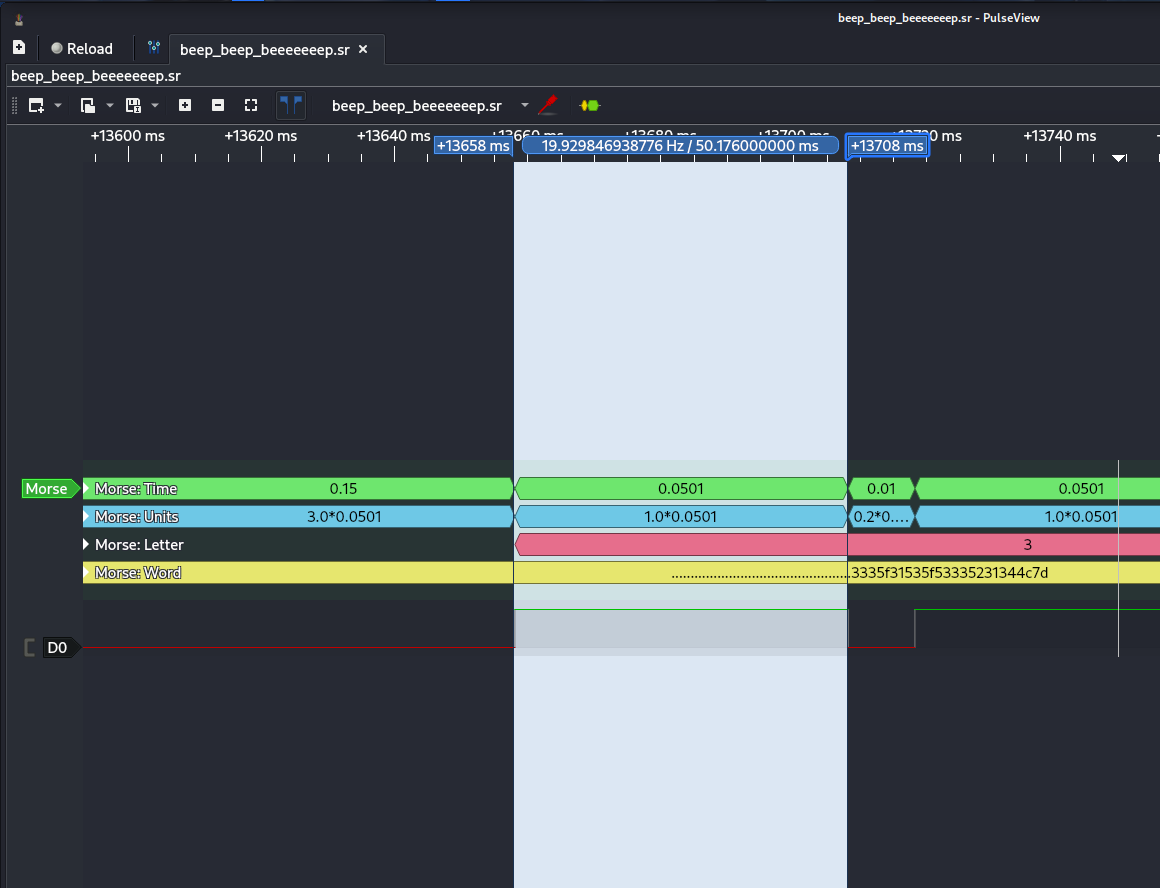
Suddenly, that noisy pattern becomes readable characters. Pretty cool, right?
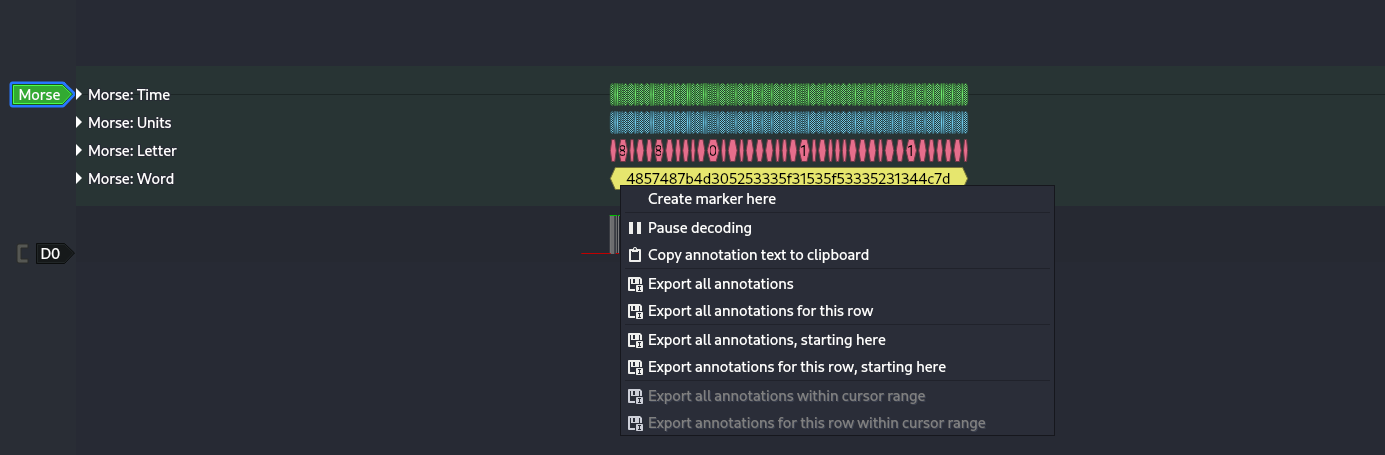
- Extract the code
Copy out the Morse results — in our case, it looked like a string of hex.
- Decode with CyberChef
Head over to CyberChef (the Swiss Army knife for data nerds).
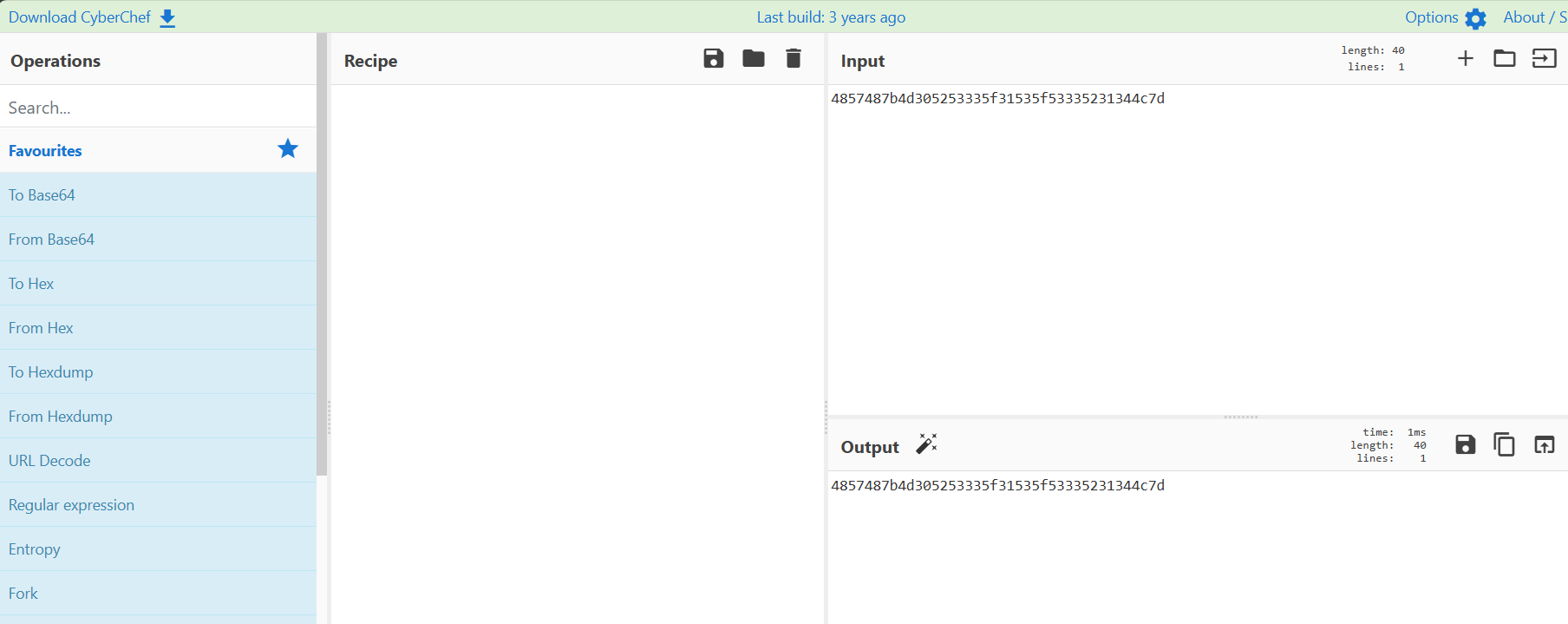
- Drop in your hex string
- Use the “From Hex” recipe
- Sit back and let the magic cook
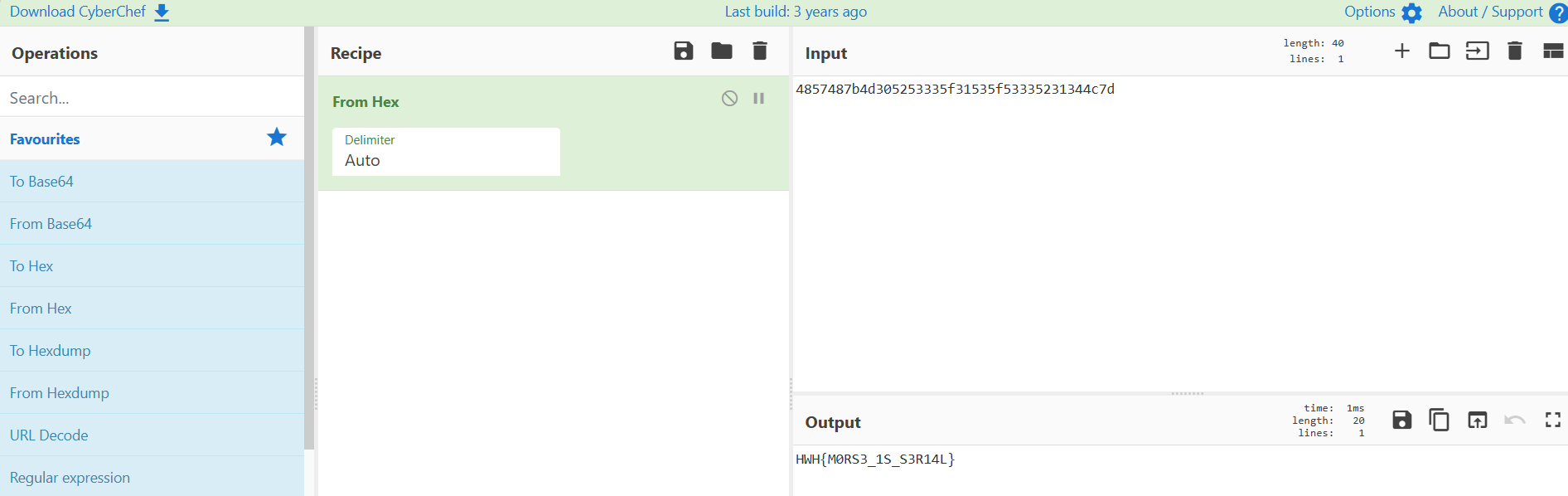
Boom. Out comes the flag:
HWH{M0RS3_1S_S3R14L}Why is this important?
This wasn’t just a fun CTF exercise — this kind of work is a mirror of real-world IoT security testing.
IoT devices:
- Often transmit sensitive data without encryption
- Can leak signals that attackers decode with simple tools
- Might use weak encodings like Morse, Base64, or XOR for “security” (spoiler: it’s not secure)
If attackers can pull data like this, so can defenders. That’s why learning SIGINT teaches us both how to attack and how to protect.
How to Prevent Signal Leaks in IoT Devices
Now, before you run off and start decoding your toaster’s Wi-Fi signals — let’s flip the snow globe and talk defense. Because every beacon you capture teaches us how to protect better.
- Encrypt Your Traffic
- Instead of raw Morse, Base64, or XOR, IoT devices should use AES or TLS encryption.
- Even lightweight devices can handle modern cryptographic libraries. If your “smart” device is transmitting in plain-text? That’s not smart at all.
- Don’t Rely on Obscurity
- Developers sometimes think: “Nobody will ever look at these signals.”
- Spoiler: Yeti just did. Obscurity ≠ security. Always assume someone is listening.
- Add Authentication & Checks
- Signals should require device authentication before being accepted.
- That means no “anyone broadcasting this pattern can control the system.”
- Rate Limit & Filter
- Prevent flooding by rejecting excessive or malformed transmissions.
- Tools like BLE filters or frequency hopping can reduce easy spam attacks.
- Regular Pentesting of IoT
- Just like web apps get tested, IoT devices need signal red-teaming.
- Run controlled exercises with tools like PulseView, HackRF, or Flipper Zero to catch weak implementations before attackers do.
Final Thoughts
Directory traversal, brute forcing, BLE spam — those are cool. But when you start pulling raw radio waves out of the air and turning them into flags? That’s next-level hacker magic.
Remember:
“Every signal tells a story. The trick is to tune your ears — and your tools — to hear it.” – 404Yeti
Stay frosty out there. 🐾
Yeti out.


