Blink to Backdoor – Yeti’s First IoT Hack

Hey snow scouts — 404Yeti here, back in the icebox with my very first IoT hacking story. And like every good IoT tale, it all begins with… a blinking LED.
That’s right: the “Hello World” of microcontrollers. But here’s the twist — what happens when that innocent blink gets weaponized into malicious firmware? Let’s find out.
The Tech
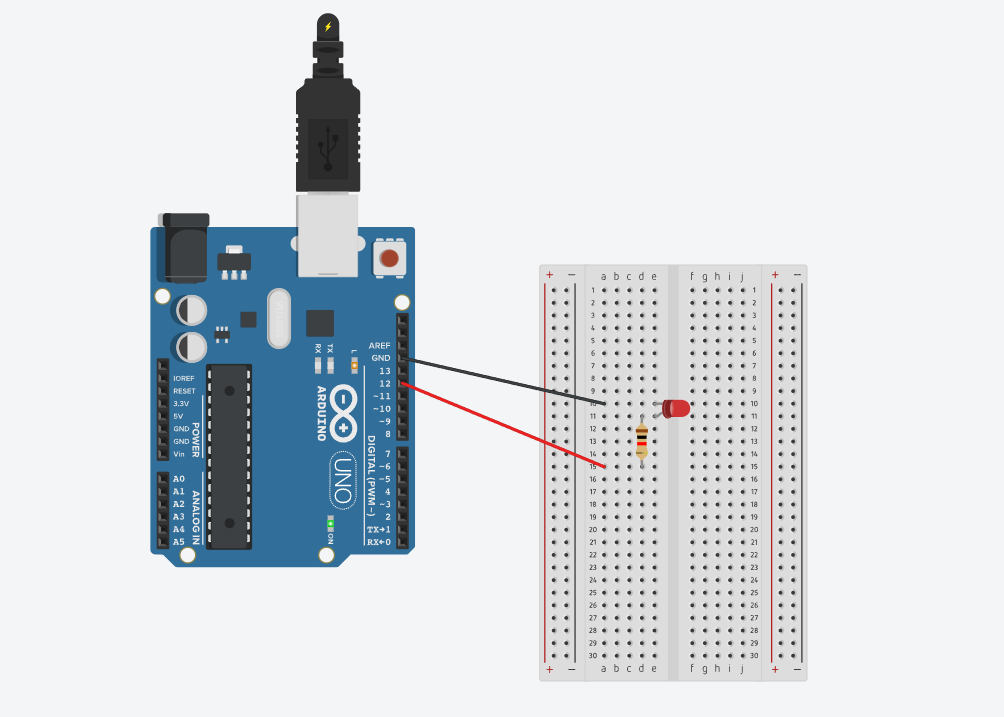
Here is a sketch of what the microcontroller is and what's attached.
- Arduino Uno
- Breadboard
- 2x jumpers
- LED light
- Resistor
Nice and simple. No frills. Just enough to make something blink… or misbehave.
The original program
This is the classic starter sketch:
void setup() {
pinMode(12, OUTPUT);
}
void loop() {
digitalWrite(12, HIGH);
delay(1000);
digitalWrite(12, LOW);
delay(1000);
}
Every second, the LED blinks on and off. The board’s way of saying, “I’m alive.”
Normal demonstration
Malicious program
Now here’s where things get spicy.
Imagine this LED wasn’t just decoration but an indicator of system health on an industrial device. If it suddenly changed its blink pattern, would you notice?
An attacker could swap the firmware to flash in Morse code, spelling out:
HACKED
const int ledPin = 12;
void dot() {
digitalWrite(ledPin, HIGH);
delay(200);
digitalWrite(ledPin, LOW);
delay(200);
}
void dash() {
digitalWrite(ledPin, HIGH);
delay(600);
digitalWrite(ledPin, LOW);
delay(200);
}
void letterSpace() { delay(600); }
void wordSpace() { delay(1400); }
void H() { dot(); dot(); dot(); dot(); }
void A() { dot(); dash(); }
void C() { dash(); dot(); dash(); dot(); }
void K() { dash(); dot(); dash(); }
void E() { dot(); }
void D() { dash(); dot(); dot(); }
void setup() {
pinMode(ledPin, OUTPUT);
}
void loop() {
H(); letterSpace();
A(); letterSpace();
C(); letterSpace();
K(); letterSpace();
E(); letterSpace();
D(); wordSpace();
}
Suddenly, your “all clear” light is literally screaming that your system has been compromised.
As I like to say:
“Sometimes the loudest alarms don’t beep — they blink.”
Malicious demonstration
Real-Life Example
This isn’t sci-fi. Researchers at Ben-Gurion University proved you can exfiltrate data from air-gapped PCs using nothing but the HDD LED.
That’s right. No Wi-Fi, no network — just blinking light leaking secrets into the dark.
If you want to read more, check it out here
Why this matters
This tiny example shows how attackers can:
- Replace firmware updates with backdoored code
- Use signals (like LED flashes) for covert data exfiltration
- Insert payloads invisible to most traditional monitoring tools
What looks like a toy project is a lesson: every hardware signal is a potential attack surface.
Prevention
- Secure Boot → Only allow cryptographically signed firmware.
- Firmware Verification → Validate updates against trusted keys.
- Access Control → Lock down debugging/programming interfaces.
- Monitoring → Alert if LED indicators behave oddly or outside spec.
“If your light blinks weird, don’t just squint at it. Audit it.” – 404Yeti
Final thoughts
What starts as a beginner’s LED project can teach us about firmware security, side-channel attacks, and why IoT deserves serious attention.
Every IoT journey begins with a blink. The question is — does that blink mean “Hello World”… or “HACKED”?
Stay frosty, stay curious.
🐾 Yeti out.
